Identity and Access Management (IAM) is the branch of IT concerned with verifying users' identity and controlling their access to digital resources. Or, as Gartner defines it: "IAM is the discipline that enables the right individuals to access the right resources at the right times for the right reasons."
IAM Key Concepts: Authentication vs. Authorization
As the name indicates, IAM concerns both verifying users' identity (authentication) and granting them access to data based on that identity (authorization). These concepts are interrelated but not interchangeable, and understanding each is critical to grasp the larger meaning of IAM.
Authentication refers to the methods you use to determine that someone is who they claim to be. The classic authentication method is the username-password combination. However, using passwords alone for authentication is increasingly regarded as insecure since passwords are easy for hackers to guess or steal via credential stuffing attacks.
Today's gold standard for verifying identity is multi-factor authentication (MFA), which supplements passwords with authentication methods that are harder to fake, such as a biometric scan or a code sent to a user's personal device.
For a real-world metaphor, imagine going to a nightclub where you're on the list. The bouncer checks your ID to make sure you're really you (authentication). Then the bouncer lets you in and tells you that there's an asterisk next to your name, which means you're allowed into the VIP section (authorization).
Authorization is the allocation or delegation of permissions to a particular individual or type of user. For example, in the nightclub, a regular patron has access to the dance floor, a VIP is allowed behind the velvet ropes, but only the owner can get into the back office with the safe.
A modern IAM platform lets admins control authorization from a central user dashboard and via APIs, saving time and preventing security incidents. For instance, you could log into your IAM dashboard and grant a specific freelancer the ability to edit their own pieces. Likewise, if an administrator leaves the company, you can revoke access, so they don't walk away with valuable intellectual property.
Types of IAM
Most organizations have multiple classes of users with different identity needs: their workforce, their business partners, and their customers. Even if you're using the same IAM platform for all three, you'll need to take a different approach for each.
Workforce identity
The average business makes use of a wide variety of applications. Say you buy and provision to your employees (like Slack or WordPress) and some you build in-house. In either case, you need a workforce IAM approach that integrates with all these disparate apps. As in our earlier example of the library, you use this to allocate permissions based on roles or individual identities.
Customer Identity (CIAM)
Customer identity and access management (CIAM) is its own branch of IAM and is used to control access to your external applications. You're most likely to use social logins here and generally focus on reducing friction (while still implementing appropriate security). CIAM is rapidly expanding as people log in on more devices, like smart TVs and wearables.
A CIAM platform is concerned not just with the end user's login experience, but with gathering information about them into a data-rich identity profile. The greater your understanding of your users, the greater your ability to provide value for them.
With this valuable data comes a huge responsibility: of obeying data privacy laws regarding data collection and storage, and sensitive data against breaches. Given that, a major (though often invisible) element of CIAM is controlling access to customer data by your own employees and third parties.
B2B identity
IAM for enterprise customers might be the most specialized branch of identity management. It's also one of the most complex since large enterprises operate on different back-end technology stacks.
Custom-made identity solutions often falter here and struggle to scale when onboarding multiple large customers. That's why startups often switch to third-party IAM platforms when they begin to move upmarket, so they can quickly federate identity using any provider and on any technology stack.
IAM Tools
An old-fashioned approach to IAM might be as simple as a login box and some basic, role-based permissions. For instance, a public library with a digital card catalog just needs to let patrons log in and ensure they can't access functions reserved for the librarians.
But that limited understanding of IAM is ill-suited to a post-digitization world. These days, most organizations utilize a vast number of applications, and personal data can be both a valuable asset and a dangerous legal liability. If that same public library wants to let patrons log into all nearby branches with the same credentials, interface with local school software to connect students with books, and simultaneously protect those students' data, they'll need a much broader set of tools than a simple login box.
Today, most IAM platforms provide some combination of the following tools and features, albeit with varying levels of customizability and extensibility.
Single Sign-On (SSO)
SSO is an IAM tool that enables a user to log into one of an organization's properties and automatically be logged into a designated set of other properties. For example, when you log into Google, you're automatically logged into your Gmail and YouTube accounts. For users, SSO reduces friction since they don't have to keep track of different credentials for every application. For organizations, SSO helps in collecting valuable insights about user behavior and preferences since it tracks them as they move from one application to another, connected by a single login.
Federated Identity
While SSO lets users log into different properties or brands owned by a single organization, federated identity does the same thing across multiple organizations.
Most people are familiar with federated identity through social login, in which you can use your Google, Facebook, or Apple ID to log into a wide range of apps. Federation is built on trust, so when you order from a food delivery app with your Apple ID, you're not ordering from Apple but indicating that the app trusts Apple enough to take their word that you are who you claim to be.
For B2B federation, there are a different set of enterprise connections, such as Active Directory, Azure, SAML, LDAP, and ADFS.
B2B federation is often a challenge because different organizations use different technology stacks and enterprise connections. But a robust IAM solution such as Auth0 integrates across numerous providers, saving companies from having to code complex workarounds to make different back ends communicate with one another.
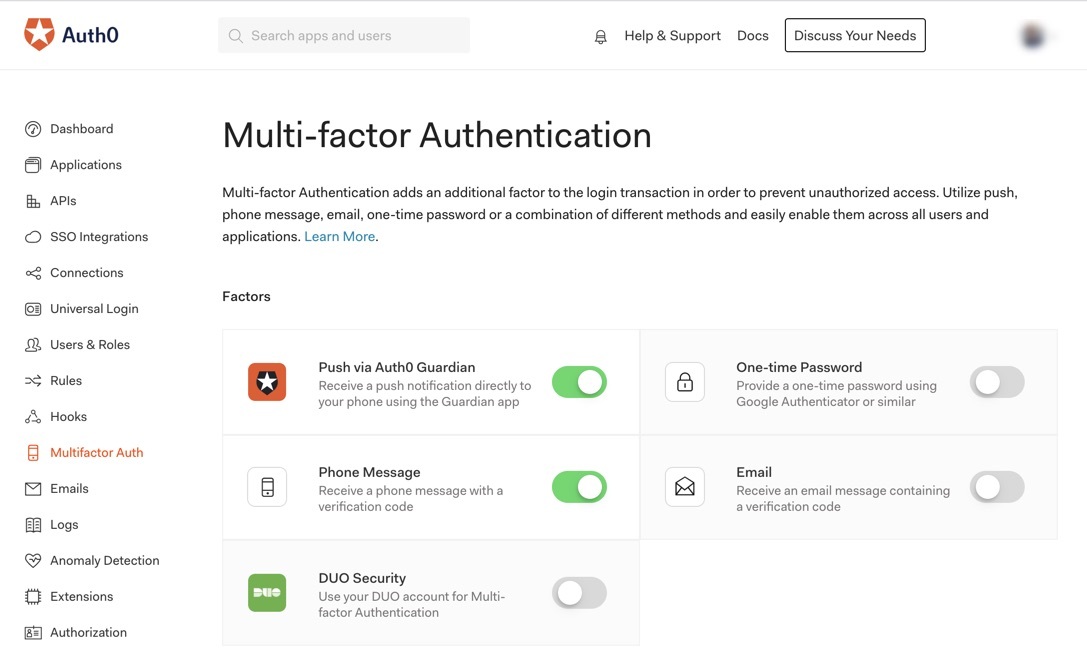
Multi-factor authentication (MFA)
As we mentioned earlier, implementing MFA is crucial to protect your organization's data from malicious intrusions, and virtually every IAM platform offers some form of MFA. However, it's equally crucial to customize MFA with the appropriate level of security. IN B2C contexts, you need to consider UX and try not to create unnecessary friction for users who don't want to be subjected to heightened scrutiny every time they log in. For workforce IAM, you may want more stringent MFA, since the consequences of an unauthorized party gaining access to your private network can be so devastating.
A modern IAM solution will allow you to implement MFA only when it's needed. This can be accomplished through step-up authentication or adaptive authentication in which users only trigger MFA if they're trying to access sensitive data or their behavior is flagged as risky.
Anomaly detection
In the past few years, identity has become the preferred gateway for hackers to break into systems. Brute force attacks, credential stuffing attacks, and even highly targeted phishing campaigns are all attempts by hackers to break in through a company's front door: the login box.
These attacks can be devastating, leading to stolen data, legal fallout, and huge spikes in traffic that crash applications. A cutting-edge IAM solution is designed to get in front of those issues through anomaly detection.
There are multiple ways IAM systems can help detect and mitigate malicious attacks. IAM solutions detect attacks by monitoring signals such as the velocity of traffic, detection of login patterns that differ from a user's routine (such as location and browser), use of a breached password, or use of devices and IP addresses with a poor reputation.
In Auth0's case, we use two primary tools for anomaly detection: brute-force protection and breached password detection.
Brute-force protection stops users from logging in from the same IP address after a certain number of failed attempts, preventing botnet attacks from causing outages.
Breached password protection is designed to monitor data breaches in which credentials have been compromised and warn both companies and individuals. Auth0's breached password protection lets users customize how they respond to such an event. Customers can notify users when their passwords have been stolen, and if they choose, prevent users from logging in until they change passwords.
The Benefits of Third-Party IAM
For users, the most visible element of IAM is the login box, but IAM's relationship to security and data management goes far beyond just usernames and passwords. Because of this, developers and IT teams are faced with a choice: build IAM functions in-house or outsource to third-party IAM platforms.
While there are advantages to each approach, a sophisticated IAM platform links identity across applications, guards against data breaches, and is a valuable source of analytics. Think of it like the circulatory system for all of an organization's digital resources — just beneath the surface, interwoven through every application.
Many companies chose to build their IAM solution in-house in years past, but these days, more and more are outsourcing their identity and access management needs to third parties. A 2020 Auth0 survey of IT professionals found that 58% currently outsource authentication when building applications. This trend has given rise to a new subset of Software as a Service (SaaS), known as Identity as a Service (IDaaS).
The reasons organizations increasingly choose to buy an IAM platform, rather than attempt to build it, are complex and vary depending on a company's size and needs.
Cost and time savings
Building and maintaining an in-house identity solution is a challenge for companies of any size and particularly for startups with limited resources. Auth0 customers frequently report that custom IAM solutions can quickly become full-time jobs for multiple developers, representing a fundamental distraction from their core business proposition.
Adaptability and extensibility
Large enterprises often transition to an external IAM provider because their in-house solution is riddled with legacy code and doesn't integrate with a wide range of applications. In-house solutions are static and closed to outsiders, and repairing one may be more of a headache than it's worth. Instead, enterprises may find more value outsourcing to a platform designed to interface with other systems and add new capabilities.
This confers major business advantages. For instance, an extensible IAM solution is crucial in post-merger integration, helping migrate user identities from multiple sources into a single directory.
Security and legal compliance
In the past few years, personal data has become a hot-button issue, with numerous high-profile data breaches and the passage of data privacy regulations around the world. Laws like GDPR and CCPA demand that businesses exercise greater control over who can access their user data and also require businesses to share that data with users upon request.
There are high costs for failing to comply with data privacy laws, and as more laws are passed, adjusting an IAM solution for each one can easily be costly. Proprietary systems often have hidden vulnerabilities and may not conform to an industry's security best practices. Outsourcing to a trusted third-party IAM platform can offload some of the burdens of compliance and ensure that security measures evolve in keeping with current best practices.
IAM: Central to Your Business, Crucial to Your Future
As you've seen, IAM is an umbrella term that encompasses multiple tools, functions, and even philosophies about how organizations manage access and identity within their systems. Many executives who aren't used to devoting much thought to IAM are surprised to learn how closely it's tied to security, user experience, and business outcomes. However, even as IAM evolves to be more important and complex, the technology for managing it is evolving to be more comprehensive and intuitive.
If you're interested in learning more about how Auth0's IAM platform can serve your identity needs, please reach out to our dedicated team.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile