What's Redis?
Redis is an in-memory key-value store that can be used as a database, cache, and message broker. The project is open source and it's currently licensed under the BSD license.
Fun Fact: Redis means "REmote DIctionary Server."
Redis delivers sub-millisecond response times that enable millions of requests per second to power demanding real-time applications such as games, ad brokers, financial dashboards, and many more!
It supports basic data structures such as strings, lists, sets, sorted sets with range queries, and hashes. More advanced data structures like bitmaps, hyperloglogs, and geospatial indexes with radius queries are also supported.
Alex Stanciu, a Product Owner from the Identity Governance Team at Auth0, explains one of our use cases for Redis:
"We use Redis as a caching layer and a session store for our Slack Bot conversation engine. Because it stores data in memory (RAM), it provides ultra-fast read and write speeds; responses are usually in the single-digit milliseconds."
In this Redis tutorial, we'll learn how to set up Redis in our systems and how to store data in Redis using its core and most frequently used data structures. With this foundation, in future posts we'll learn how to use Redis for caching, session storage, messaging, and real-time analytics. Let's get started!
Installing Redis
The first thing that we need to do is install Redis. If you have it already running in your system, feel free to skip this part of the post.
The Redis documentation recommends installing Redis by compiling it from sources as Redis has no dependencies other than a working
GCC compilerlibcredis.iohttp://download.redis.io/redis-stable.tar.gzWindows users: The Redis project does not officially support Windows. But, if you are running Windows 10, you can Install the Windows Subsystem for Linux to install and run Redis. When you have the Windows Subsystem for Linux up and running, please follow any steps in this post that apply to Linux (when specified) from within your Linux shell.
To compile Redis follow these simple steps:
- Create a
directory and make it the current working directory:redis
macOS/Linux:
mkdir redis && cd redis
- Fetch the latest redis tarball:
macOS/Linux:
curl -O http://download.redis.io/redis-stable.tar.gz
- Unpack the tarball:
macOS/Linux:
tar xvzf redis-stable.tar.gz
- Make the unpacked
directory the current working directory:redis-stable
macOS/Linux:
cd redis-stable
- Compile Redis:
macOS/Linux:
make
If the
package is not installed in your system, please follow the instructions provided by the CLI to install it. In macOS, you may need to download XCode to have access to the command line tools which includemakeand a C compiler. For a fresh installation of Ubuntu, for example, you may want to run the following commands to update the package manager and install core packages:make
Ubuntu:
sudo apt update sudo apt upgrade sudo apt install build-essential sudo apt-get install tcl8.5 make
tcl- Test that the build works correctly:
macOS/Linux:
make test
Once the compilation is done, the
srcredis-stable
: runs the Redis Server itself.redis-server
: runs Redis Sentinel, a tool for monitoring and failover.redis-sentinel
: runs a command line interface utility to interact with Redis.redis-cli
: checks Redis performance.redis-benchmark
andredis-check-aof
: used for the rare cases when there are corrupted data files.redis-check-dump
We are going to be using the
redis-serverredis-climacOS/Linux:
sudo cp src/redis-server /usr/local/bin/ sudo cp src/redis-cli /usr/local/bin/
While having
redis-stablemacOS/Linux:
sudo make install
We need to restart our shell for these changes to take effect. Once we do that, we are ready to start running Redis.
Running Redis
Starting Redis
The easiest way to start the Redis server is by running the
redis-serverredis-server
If everything is working as expected, the shell will receive as outline a giant ASCII Redis logo that shows the Redis version installed, the running mode, the
portPID_._ _.-``__ ''-._ _.-`` `. `_. ''-._ Redis 4.0.10 (00000000/0) 64 bit .-`` .-```. ```\/ _.,_ ''-._ ( ' , .-` | `, ) Running in standalone mode |`-._`-...-` __...-.``-._|'` _.-'| Port: 6379 | `-._ `._ / _.-' | PID: 22394 `-._ `-._ `-./ _.-' _.-' |`-._`-._ `-.__.-' _.-'_.-'| | `-._`-._ _.-'_.-' | http://redis.io `-._ `-._`-.__.-'_.-' _.-' |`-._`-._ `-.__.-' _.-'_.-'| | `-._`-._ _.-'_.-' | `-._ `-._`-.__.-'_.-' _.-' `-._ `-.__.-' _.-' `-._ _.-' `-.__.-'
We started Redis without any explicit configuration file; therefore, we'll be using the internal default configuration. This is acceptable for the scope of this blog post: understanding and using the basic Redis data structures.
As a first step, we always need to get the Redis server running as the CLI and other services depend on it to work.
How to Check if Redis is Working
As noted in the Redis docs, external programs talk to Redis using a TCP socket and a Redis specific protocol. The Redis protocol is implemented by Redis client libraries written in many programming languages, like JavaScript. But we don't need to use a client library directly to interact with Redis. We can use the
redis-clipingredis-cli ping
If everything is working well, we should get
PONGWhen we issued
redis-cli pingredis-clipinglocalhost:6379The host and port of the instance can be changed. Use the
--helpredis-cliredis-cli --help
If we run
redis-cliLet start first by learning how to manipulate data in Redis using commands!
“Redis is a key-value store that let us store some data, the value, inside a key. It offers ultra-fast performance to satisfy demanding real-time applications like video games 🎮.”
Tweet This
Write, Read, Update, and Delete Data in Redis
As we learned earlier, Redis is a key-value store that let us associate some data called a value with a key. We can later retrieve the stored data if we know the exact key that was used to store it.
In case that you haven't done so already, run the Redis CLI in interactive mode by executing the following command:
redis-cli
We'll know the interactive CLI is working when we see the Redis instance host and port in the shell prompt:
127.0.0.1:6379>
Once there, we are ready to issue commands.
Writing Data
To store a value in Redis, we can use the
command which has the following signature:SET
SET key value
In English, it reads like "set key to hold value." It's important to note that if the key already holds a value,
SETLet's look at an example. In the interactive shell type:
SET service "auth0"
Notice how, as you type, the interactive shell suggests the required and optional arguments for the Redis command.
Press
enter"auth0"serviceOKReading Data
We can use the
command to ask Redis for the value of a key:GET
GET key
Let's retrieve the value of
serviceGET service
Redis replies with
"auth0"What if we ask for the value of a key that has never been set?
GET users
Redis replies with
(nil)In a classic API that connects to a database, we'd like to perform CRUD operations: create, read, update, and delete. We have covered how to create (write) and read data in Redis by using the
SETGETUpdating Data
We can update the value of a key simply by overwriting its data as mentioned earlier.
Lets create a new key-value pair:
SET framework angular
But, we change our mind and now we want the value to be
"react"SET framework react
Did Redis get it right? Let's ask for it!
GET framework
Redis indeed replies with
"react"framework"vue"SET framework vue
If we run
GET framework"vue"Deleting Data
But, we don't want to actually set any framework for now and we need to delete that key. How do we do it? We use the
command:DEL
DEL key
Let's run it:
DEL framework
Redis replies with
(integer) 1With just three commands,
SETGETDELWrapping Strings with Quotation Marks
Notice something curious: we did not have to put quotation marks around a single string value we wanted to store.
SET framework angularSET framework "angular""angular"frameworkRedis automatically wraps single string arguments in quotation marks. Since both key and value are strings, the same applies for the key name. We could have used
SET "framework" angularSET "the frameworks" "angular vue react"
Replies with
OKSET the frameworks "angular vue react"
Replies with
(error) ERR syntax errorSET "the frameworks" angular vue react
Also replies with
(error) ERR syntax errorFinally, to retrieve the value, we must use the exact key string:
GET "the frameworks"
Replies with
"angular vue react"Non-Destructive Write
Redis is compassionate and lets us write data with care. Imagine that we wanted to create a
services"heroku aws"SET services "heroku aws"SET service "heroku aws"serviceSETSETNXSETNX key value
SETNXSETNX01SETNXSETSETNX service "heroku aws"
The reply is
(integer) 0SETNX services "heroku aws"
This time, the reply is
(integer) 1We can use
SETNXExpiring Keys
When creating a key with Redis, we can specify how long that key should stay stored in memory. Using the
command, we can set a timeout on a key and have the key be automatically deleted once the timeout expires:EXPIRE
EXPIRE key seconds
Let's create a
notificationSET notification "Anomaly detected" EXPIRE notification 30
This schedules the
notificationnotificationTTLTTL key
It's possible that more than 30 seconds have already passed so let's try the above example again, but this time calling
TTLEXPIRESET notification "Anomaly detected" EXPIRE notification 30 TTL notification
Redis replied with
(integer) 27notificationTTLTTL notification
This time, Redis replied with
(integer) -2TTL- The timeout left in seconds.
if the key doesn't exist (either it has not been created or it was deleted).-2
if the key exists but has no expiry set.-1
I made sure that 30 seconds had passed so
-2SET dialog "Continue?" TTL dialog
As expected, with no expiry set, Redis replies with
(integer) -1It's important to note that we can reset the timeout by using
SETSET notification "Anomaly detected" EXPIRE notification 30 TTL notification // (integer) 27 SET notification "No anomaly detected" TTL notification // (integer) -1
We learned earlier that using
SETWe have a solid foundation now on manipulating data in Redis. With this knowledge under our belt, we are ready to now explore the data types that Redis offers.
Redis Data Types
Far from being a plain key-value store, Redis is an actual data structure server that supports different kinds of values. Traditionally, key-value stores allow us to map a string key to a string value and nothing else. In Redis, the string key can be mapped to more than just a simple string.
Being a data structure server, we can also refer to the data types as data structures. We can use these more complex data structures to store multiple values in a key at once. Let's look at these types at a high level. We'll explore each type in detail in subsequent sections.
- Binary-safe Strings
The most basic kind of Redis value. Being "binary-safe" means that the string can contain any type of data represented as a string: PNG images or serialized objects, for example.
- Lists
In essence, Redis Lists are linked lists. They are collections of string elements that are sorted based on the order that they were inserted.
- Sets
They represent collections of unique and unsorted string elements.
- Sorted Sets
Like Sets, they represent a collection of unique string elements; however, each string element is linked to a floating number value, referred to as the element score. When querying the Sorted Set, the elements are always taken sorted by their score, which enables us to consistently present a range of data from the Set.
- Hashes
These are maps made up of string fields linked to string values.
- Bit arrays
Also known as bitmaps. They let us handle string values as if they were an array of bits.
- HyperLogLogs
A probabilistic data structure used to estimate the cardinality of a set, which is a measure of the "number of elements of the set."
We have already covered Strings during the "Write, Read, Update, and Delete Data in Redis" section. For the rest of this tutorial, we are going to focus on all the Redis types except bitmaps and hyperloglogs. We'll visit those on a future post handling an advanced Redis use case.
Every time some site gets “slashdotted“ and is no longer reachable, I think at my little blog in a 5$/mo VM that resists any HN top position pressure without being even remotely affected. And think that many people are sincerely missing an opportunity to use Redis.
— ANTIREZ (@antirez) July 12, 2018
Lists
A List is a sequence of ordered elements. For example,
1 2 4 5 6 90 19 3A List is created by using a Redis command that pushes data followed by a key name. There are two commands that we can use:
RPUSHLPUSHRPUSH
inserts a new element at the end of the List (at the tail):RPUSH
RPUSH key value [value ...]
Let's create an
engineersRPUSH engineers "Alice" // 1 RPUSH engineers "Bob" // 2 RPUSH engineers "Carmen" // 3
Each time we insert an element, Redis replies with the length of the List after that insertion. We would expect the
usersAlice Bob Carmen
How can we verify that? We can use the
LRANGELRANGE
LRANGELRANGE key start stop
To see the full List, we can use a neat trick: go from
0-1LRANGE engineers 0 -1
Redis returns:
1) "Alice" 2) "Bob" 3) "Carmen"
The index
-1To get the first two elements of
engineersLRANGE engineers 0 1
LPUSH
behaves the same as LPUSH
RPUSHLPUSH key value [value ...]
Let's insert
DanielengineersLPUSH engineers "Daniel" // 4
We now have four engineers. Let's verify that the order is correct:
LRANGE engineers 0 -1
Redis replies with:
1) "Daniel" 2) "Alice" 3) "Bob" 4) "Carmen"
It's the same List we had before but with
"Daniel"Multiple Element Insertions
We saw in the signatures of
RPUSHLPUSHBased on our existing
engineersRPUSH engineers "Eve" "Francis" "Gary" // 7
Since we are inserting them at the end of the List, we expect these three new elements to show up in the same order in which they are listed as arguments. Let's verify:
LRANGE engineers 0 -1
To what Redis returns:
1) "Daniel" 2) "Alice" 3) "Bob" 4) "Carmen" 5) "Eve" 6) "Francis" 7) "Gary"
What about if we do the same with
LPUSHLPUSH engineers "Hugo" "Ivan" "Jess" // 10
Will Redis insert these three new elements one by one or will it insert them as a bundle, all three at once?
Let's see:
LRANGE 0 -1
Reply:
1) "Jess" 2) "Ivan" 3) "Hugo" 4) "Daniel" 5) "Alice" 6) "Bob" 7) "Carmen" 8) "Eve" 9) "Francis" 10) "Gary"
When listing multiple arguments for
LPUSHRPUSH"Hugo""Ivan""Jess"LLEN
We can find the length of a List at any time by using the
command:LLEN
LLEN key
Let's verify that the length of
engineers10LLEN engineers
Redis replies with
(integer) 10Removing Elements from a Redis List
Similar to how we can "pop" elements in arrays, we can pop an element from the head or the tail of a Redis List.
removes and returns the first element of the List:LPOP
LPOP key
We can use it to remove
"Jess"LPOP engineers
Redis indeed replies with
"Jess"
removes and returns the last element of the List:RPOP
RPOP key
It's time to say goodbye to
"Gary"RPOP engineers
The reply from Redis is
"Gary"It's very useful to be able to get the element that was removed from the List as we may want to do something special with it.
Redis Lists are implemented as linked lists because its engineering team envisioned that for a database system it is crucial to be able to add elements to a very long list in a very fast way.
Sets
In Redis, a Set is similar to a List except that it doesn't keep any specific order for its elements and each element must be unique.
SADD
We create a Set by using the
command that adds the specified members to the key:SADD
SADD key member [member ...]
Specified members that are already part of the Set are ignored. If the key doesn't exist, a new Set is created and the unique specified members are added. If the key already exists or it is not a Set, an error is returned.
Let's create a
languagesSADD languages "english" // 1 SADD languages "spanish" // 1 SADD languages "french" // 1
In this case, on each member addition Redis returns the number of members that were added with the
SADDSADD languages "chinese" "japanese" "german" // 3 SADD languages "english" // 0
The first command returned
30"english"SREM
We can remove members from a Set by using the
command:SREM
SREM key member [member ...]
We can remove one or more members at the same time:
SREM languages "english" "french" // 2 SREM languages "german" // 0
SREMSISMEMBER
To verify that a member is part of a Set, we can use the
command:SISMEMBER
SISMEMBER key member
If the member is part of the Set, this command returns
10SISMEMBER languages "spanish" // 1 SISMEMBER languages "german" // 0
Since we removed
"german"0SMEMBERS
To show all the members that exist in a Set, we can use the
command:SMEMBERS
SMEMBERS key
Let's see what language values we currently have in the
languagesSMEMBERS languages
Redis returns:
1) "chinese" 2) "japanese" 3) "spanish"
As Sets are not ordered, Redis is free to return the elements in any order at every call. They have no guarantees about element ordering.
SUNION
Something really powerful that we can do with Sets very fast is to combine them using the
command:SUNION
SUNION key [key ...]
Each argument to
SUNIONTo see this in action, let's first create an
ancient-languagesSADD ancient-languages "greek" SADD ancient-languages "latin" SMEMBERS ancient-languages
Now, let's create a union of
languagesancient-languagesSUNION languages ancient-languages
We get the following reply:
1) "greek" 2) "spanish" 3) "japanese" 4) "chinese" 5) "latin"
If we pass to
SUNIONHashes
In Redis, a Hash is a data structure that maps a string key with field-value pairs. Thus, Hashes are useful to represent objects. They
keyvaluefield-name field-valuecomputercomputer name "MacBook Pro" year 2015 disk 512 ram 16
The "properties" of the object are defined as sequences of "property name" and "property value" after the name of the object,
computerTo manipulate Hashes, we use commands that are similar to what we used with strings, after all, they are strings.
Writing and Reading Hash Data
HSET
The command
sets HSET
fieldvaluekeyfieldHSET key field value
Let's create the
computerHSET computer name "MacBook Pro" // 1 HSET computer year 2015 // 1 HSET computer disk 512 // 1 HSET computer ram 16 // 1
For each
HSET
if1
is a new field in the hash and value was set.field
if0
already exists in the hash and the value was updated.field
Let's update the value of the
year2018HSET computer year 2018 // 0
HGET
returns the value associated with HGET
fieldHGET key field
Let's verify that we are getting
2018year2015HGET computer year
Redis replies with
"2018"HGETALL
A fast way to get all the fields with their values from the hash is to use
:HGETALL
HGETALL key
Let's test it out:
HGETALL computer
Reply:
1) "name" 2) "MacBook Pro" 3) "year" 4) "2018" 5) "disk" 6) "512" 7) "ram" 8) "16"
HGETALLkeyHMSET
We can also set multiple fields at once using
HMSETHMSET key field value [field value ...]
Let's create a
tabletHMSET tablet name "iPad" year 2016 disk 64 ram 4
HMSETOKtabletHMGET
What if we want to get just two fields? We use
to specify from which fields in the hash we want to get a value:HMGET
HMGET key field [field ...]
Let's get the
diskramtabletHMGET tablet disk ram
Effectively we get the values of
diskram1) "64" 2) "4"
That's pretty much the gist of using Hashes in Redis. You may explore the full list of Hash commands and try them out.
Sorted Sets
Introduced in Redis 1.2, a Sorted Set is, in essence, a Set: it contains unique, non-repeating string members. However, while members of a Set are not ordered (Redis is free to return the elements in any order at every call of a Set), each member of a Sorted Set is linked to a floating point value called the score which is used by Redis to determine the order of the Sorted Set members. Since, every element of a Sorted Set is mapped to a value, it also has an architecture similar to Hash.
In Redis, a Sorted Set could be seen as a hybrid of a Set and a Hash.
How is the order of members of a Sorted Set determined? As stated in the Redis documentation:
- If A and B are two members with a different score, then A > B if A.score is > B.score.
- If A and B have exactly the same score, then A > B if the A string is lexicographically greater than the B string. A and B strings can't be equal since Sorted Sets only have unique elements.
Some of the commands that we use to interact with Sorted Sets are similar to the commands we used with Sets: we replace the
SZSADDZADDZADD
Using
adds all the specified members with specified scores to the Sorted Set:ZADD
ZADD key [NX|XX] [CH] [INCR] score member [score member ...]
As with Sets, if
keykeyStarting in Redis 3.0.2,
has optional arguments that gives us control of insertions:ZADD
: Only update members that already exist. Never add members.XX
: Don't update already existing members. Always add new members.NX
: Modify the return value from the number of new members added, to the total number of members changed (CH is an abbreviation of changed). Changed members are new members added and members already existing for which the score was updated. So members specified in the command line having the same score as they had in the past are not counted.CH
: When this option is specified ZADD acts likeINCR
. Only one score-members pair can be specified in this mode.ZINCRBY
It's good to know that these optional arguments are there and what they do, but for this introduction, we are going to focus on adding members without using any of them, but feel free to explore them! In future posts, we are going to revisit them in more complex use cases!
Let's create a Sorted Set to store Help Desk Support tickets. Support tickets are meant to be unique but also need to be sorted, hence, this data structure is a great choice:
ZADD tickets 100 HELP204 // 1 ZADD tickets 90 HELP004 // 1 ZADD tickets 180 HELP330 // 1
ZADDZRANGE
We'd like now to see how our Sorted Set looks. With Sets, we used
SMEMBERS
returns the specified range of members in the Sorted Set:ZRANGE
ZRANGE key start stop [WITHSCORES]
It behaves very similarly to
LRANGE0 -1ZRANGE tickets 0 -1
Redis replies with:
1) "HELP004" 2) "HELP204" 3) "HELP330"
We can pass
ZRANGEWITHSCORESZRANGE tickets 0 -1 WITHSCORES
Reply:
1) "HELP004" 2) "90" 3) "HELP204" 4) "100" 5) "HELP330" 6) "180"
Notice how the
memberscoreticketsUsing Redis as a Session Store
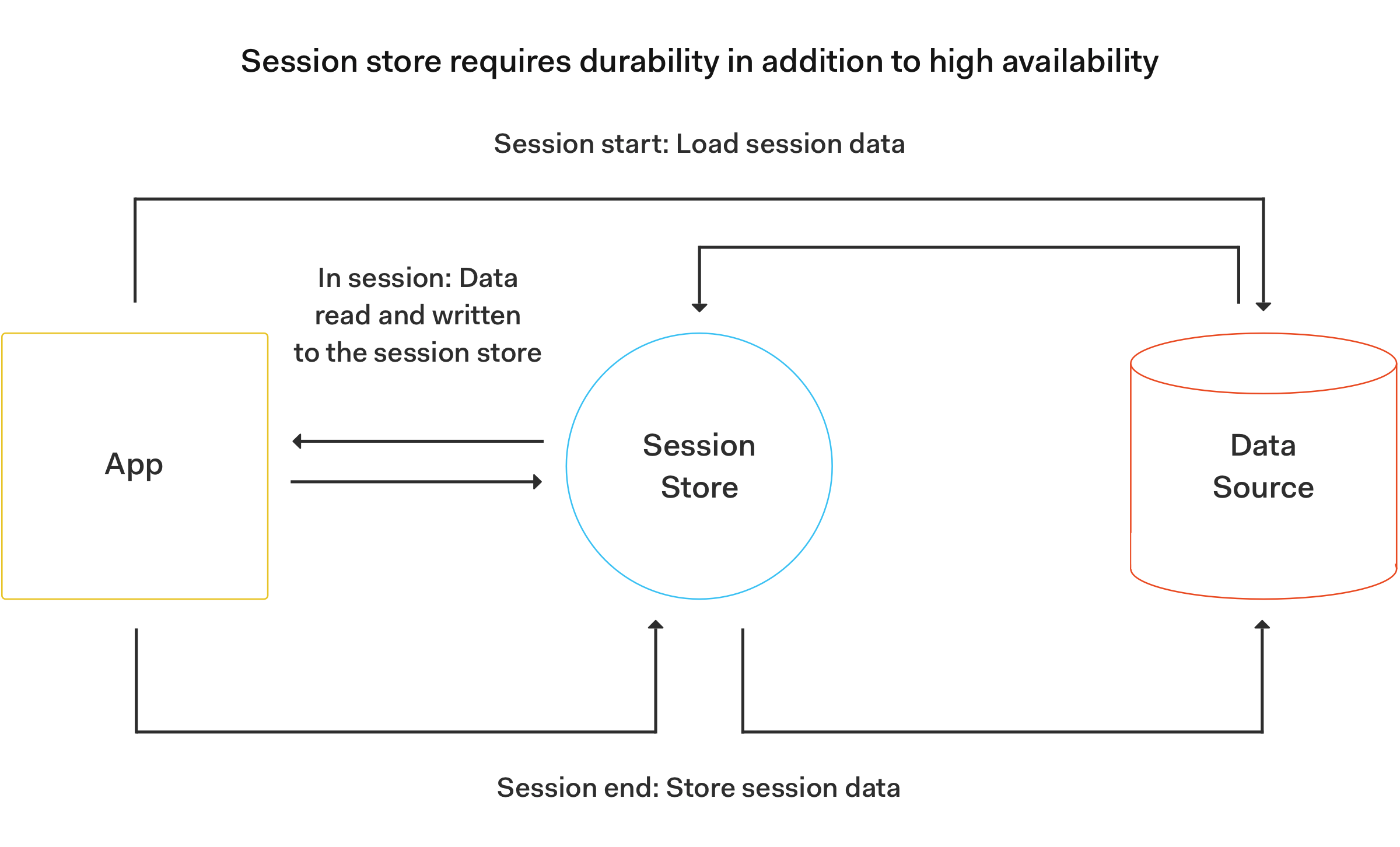
The most relevant use of Redis in the authentication and authorization workflows of a web application is to serve as a session store.
As recognized by Amazon Web Services, the in-memory architecture of Redis provides developers with high availability and persistence that makes it a popular choice to store and manage session data for internet-scale applications. Its lightning-fast performance provides us with the super low latency, optimal scale, and resiliency that we need to manage session data such as user profiles, user settings, session state, and credential management.
Roshan Kumar, from Redis, explains on his "Cache vs. Session Store" article that a session-oriented web application starts a session when the user logs in. The session is active until the user logs out or the session times out. During the session lifecycle, the web application stores all session-related data in the main memory (RAM) or in a session store that doesn't lose the data when the application goes down. This session store can be implemented using Redis that, despite being an in-memory store, is able to persist data by writing transaction logs sequentially in the disk.
Source: Redis: Cache vs. Session Store
Roshan further explains that session stores rely on reading and writing data to the in-memory database. The session store data isn’t temporary and it becomes the only source of truth when the session is live. For that reason, the session store needs to meet the "data durability requirements of a true database."
“According to @Redisinc, a session store requires high availability and durability to support transactional data and uninterrupted user engagement. You can achieve that easily using #Redis.”
Tweet This
Conclusion
Redis is a powerful, nimble, and flexible database that can speed up your architecture. It has a lot to offer including caching, data replication, pub/sub messaging systems, session storage, and much more. Redis has a multitude of clients that cover all of the popular programming languages. I hope that you try it out whenever you have a use case that fits its value propositions.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Dan Arias
Staff Developer Advocate
The majority of my engineering work revolves around AWS, React, and Node, but my research and content development involves a wide range of topics such as Golang, performance, and cryptography. Additionally, I am one of the core maintainers of this blog. Running a blog at scale with over 600,000 unique visitors per month is quite challenging!
I was an Auth0 customer before I became an employee, and I've always loved how much easier it is to implement authentication with Auth0. Curious to try it out? Sign up for a free account ⚡️.View profile