If you're a growing company, particularly one that deals with a large volume of customer information, it's critical to know what solutions are available to help you protect all of this sensitive data.
The phrase identity as a service (or IDaaS) comes up repeatedly in conversations about protecting users. In the wake of scandals like Facebook's, many companies are turning to identity as a service providers to help them secure and manage online identities.
But what exactly is identity as a service? What do these providers actually offer that can help you in such a challenging environment?
In this piece, we define identity as a service and break it down into core components that can help teams be more secure.
IDaaS Defined
Identity as a service (IDaaS) comprises cloud-based solutions for identity and access management (IAM) functions, such as single sign-on (SSO). These methods allow all users (customers, employees, and third parties) to more securely access sensitive information both on and off-premises.
IDaaS also means collecting intelligence (i.e., logging events and reporting on which users accessed what information and when) to better understand, monitor, and improve their behaviors.
Multi-factor authentication (MFA), including biometrics, are core components of IDaaS.
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) is an increasingly popular way of verifying a user's identity. MFA requires more than one piece of identifying information (i.e., a password).
Typically, two or more of the following criteria are used:
- Knowledge: Something the user knows (such as a password)
- Possession: Something the user has (such as a cell phone)
- Inheritance: Something the user is (such as a fingerprint or retina scan)
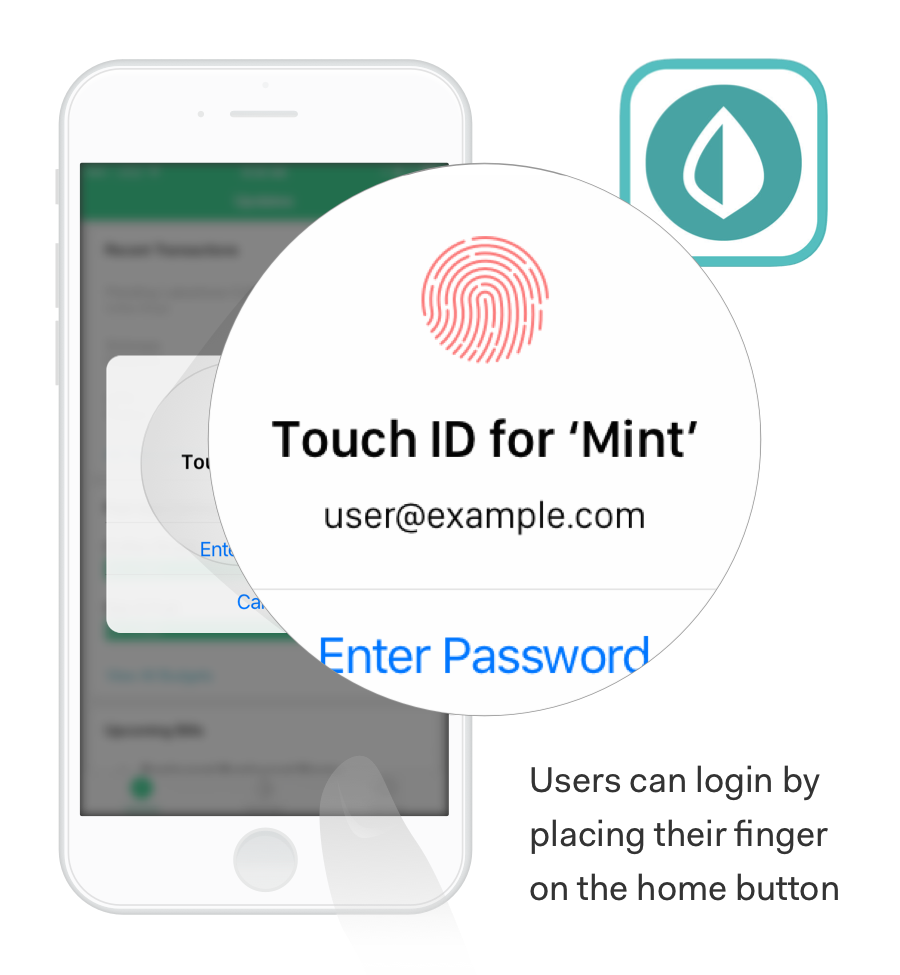
For example, some apps like Intuit Mint have implemented Touch ID.
In order to enter the app, a user must possess their cell phone and know their password.
Multi-factor or two-factor authentication provides an additional layer of security and diminishes the likelihood of unauthorized access. If a cyber thief gets ahold of your password, they still won't be able to access your account without your thumb and phone.
Google 2-Step Verification and Microsoft Authenticator are other examples of how multi-factor authentication can work. Both of these rely on a TOTP (time-based one-time password algorithm).
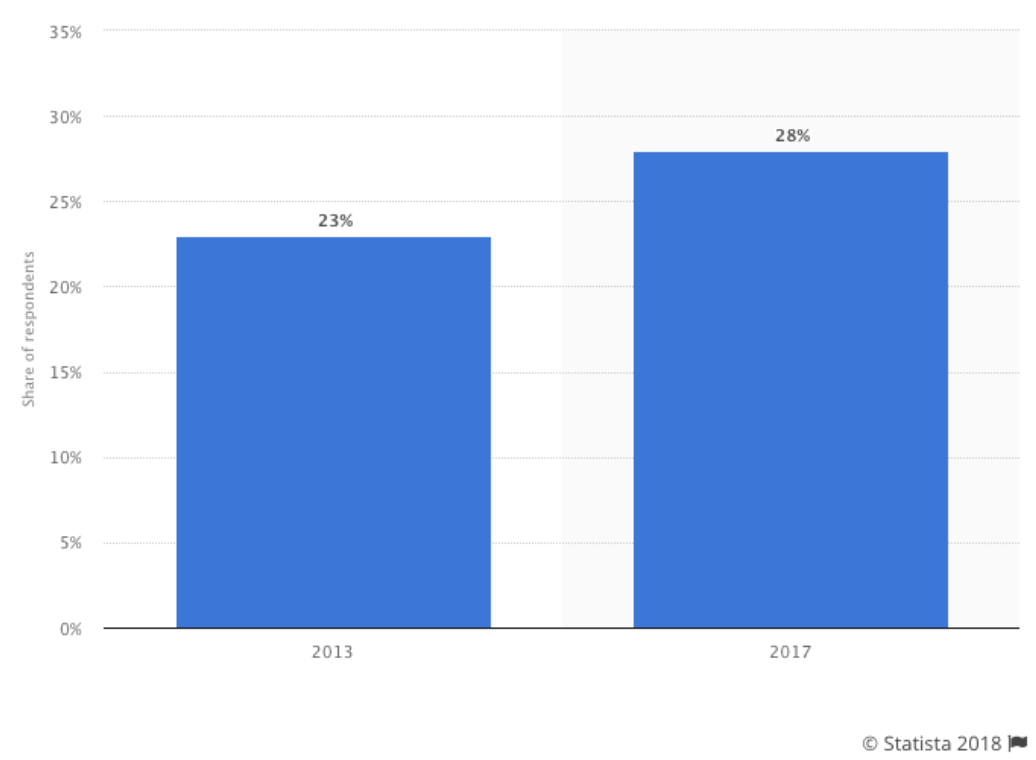
Despite numerous reports on the benefits of multi-factor authentication for stopping data breaches, widespread adoption is still low:
(Source)
One of the reasons for this is that it's relatively technical to get going — and users must be involved. Full deployment often requires issuing tokens or embedding cryptographic keys in specific devices.
Multi-factor authentication is also not bulletproof (although it is certainly safer than a simple password-protected system). New and safer iterations of multi-factor authentication are becoming popular, such as biometrics.
Biometrics
Biometrics means the use of an "inheritance" criteria — something the user is as a means of verification.
In addition to touch ID, other common multi-factor authentication methods include SMS and voice verifications.
Some teams are even turning to thumbprints, iris or retina recognition, full facial recognition, fingerprint, hand, and DNA usage.
Additional emerging technologies include:
Voice recognition. (Auth0 already has a means of helping users authenticate via voice recognition with our partner, Twilio.)
Typing recognition. (While this has been slower to stick in U.S. markets, many financial firms in Norway have widely adopted the strategy. One company boasted a 99.7% success rate for distinguishing real users from fake.)
Body modifications (body mod) is one more pioneering method.
Above, a senior BuzzFeed reporter implanted a chip in his hand and successfully purchased goods by connecting it to a mobile paying app.
While many of these represent exciting new frontiers for biometrics and multi-factor authentication, Touch ID, SMS, and voice verifications are good places to begin.
New Regulations to Help Protect Users' Identities
One of the reasons that IDaaS has become so important recently is the rush to comply with the EU's General Data Protection Regulation (GDPR). Officially approved April 14, 2016, GDPR officially became enforceable May 25, 2018. It applies to all businesses globally that collect and process the data of EU citizens.
A slew of other related regulations are springing up, such as the California Consumer Privacy Act (CCPA).
Today, organizations that are audited and don't have adequate security measures in place for consumer data can be fined up to 20 million euros or 4 percent of annual global turnover — whichever is higher.
Despite these stiff punishments, a lot of companies are far from ready. Studies show that in Ireland, for example, a quarter of organizations would be forced to shut down if audited — and 60% of tech companies aren't fully prepared.
This opens more possibilities for IDaaS providers in 2018. Strong, flexible identity management is essential to keeping user identities safe and allowing them to comply with the new GDPR rules like:
- A new Right to Data Portability
- An extended Right to Be Forgotten (also called the Right to Erasure)
- An enhanced Subject Access Right - to be free and with a shorter time to reply
Although an IDaaS provider like Auth0 can't ensure your organization will be fully compliant, we have lots of tools that can help.
IDaaS and Blockchain
2017 and 2018 have been enormous years for Bitcoin, Ethereum, and other cryptocurrencies. Although the technology remains divisive (PwC calls cryptocurrencies one of the "greatest technological breakthroughs since the Internet," while others describe them as a money-sucking "black holes"), it still highlights some incredible IDaaS opportunities.
The decentralized nature of blockchain avoids large, consolidated pools of data, which are ripe for hackers. Distributed ledgers can separate personal data, duplicate it thousands of times, and disperse it globally — but true ownership of the data remains with the individual.
While no one truly knows how (or whether) blockchain will definitely be used to manage personal identities going forward, many argue that because of its success in tracking inventory and payments, similar techniques could help verify individuals and their behaviors.
What's Ahead for IDaaS
Demand from new regulations, paired with a lot of excitement and funding for new solutions, has opened a lot of avenues for IDaaS.
Teams of all sizes are taking security seriously and making investments so they can move forward with less worry.
Incorporating tactics like multi-factor authentication, including biometrics like Touch ID, making sure you're in compliance with GDPR and other identity regulations, and even brainstorming how blockchain might help verify your users in the future will help your team secure its most critical data so you can grow safely.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile