The tension between freedom for users and manageability for enterprises can lead to security problems.
Employees want the freedom to do what they want and the flexibility to do it on the devices they prefer. IT wants the ability to manage, and secure, the waves of devices and applications accessing their networks. The threat of slowing down or waiting for IT can tempt employees to seek workarounds.
A Nintex study found that 40% of surveyed employees used unapproved devices or apps because IT failed to provide prompt service. This isn't just users vs. IT: that same survey showed that nearly two-thirds of IT sought workarounds, too. This is a symptom of that underlying tension between freedom and manageability.
This tension only worsens as mobile security threats get more dangerous. The possibility of damaging data breaches is forcing enterprises to reconsider their enterprise mobility strategy.
Mobile devices aren't going away — and neither are the threats that make them risky. Here are three ways to ensure security remains a priority as enterprise mobility evolves.
Where Does Device Security Fit into Enterprise Mobility Strategies?
The harder it is to manage enterprise mobile devices, the harder it is to ensure their security. This conflict creates divergent mobility strategies.
Most companies are embracing bring-your-own-device (BYOD) policies, even though nearly a third cite security as the strategy's top challenge. Other companies are paying monthly, per-device licenses for enterprise mobility management (EMM) products that promise visibility and security.
Mobile devices present unique vulnerabilities that demand security strategies across the device mobility spectrum, including mobile applications, content, and identity.
Employees bringing consumer devices into the enterprise might be bringing their bad habits, too. According to a Pew Research study, more than a quarter of smartphone users don't use a lock screen, which would leave data and credentials exposed if the device were stolen or lost.
With the rise of remote work, bad security habits can follow people around the globe. The coffee shop might be a picturesque place to work, but its public wi-fi could offer a hacker the opportunity to steal your employee's credentials and access precious company data.
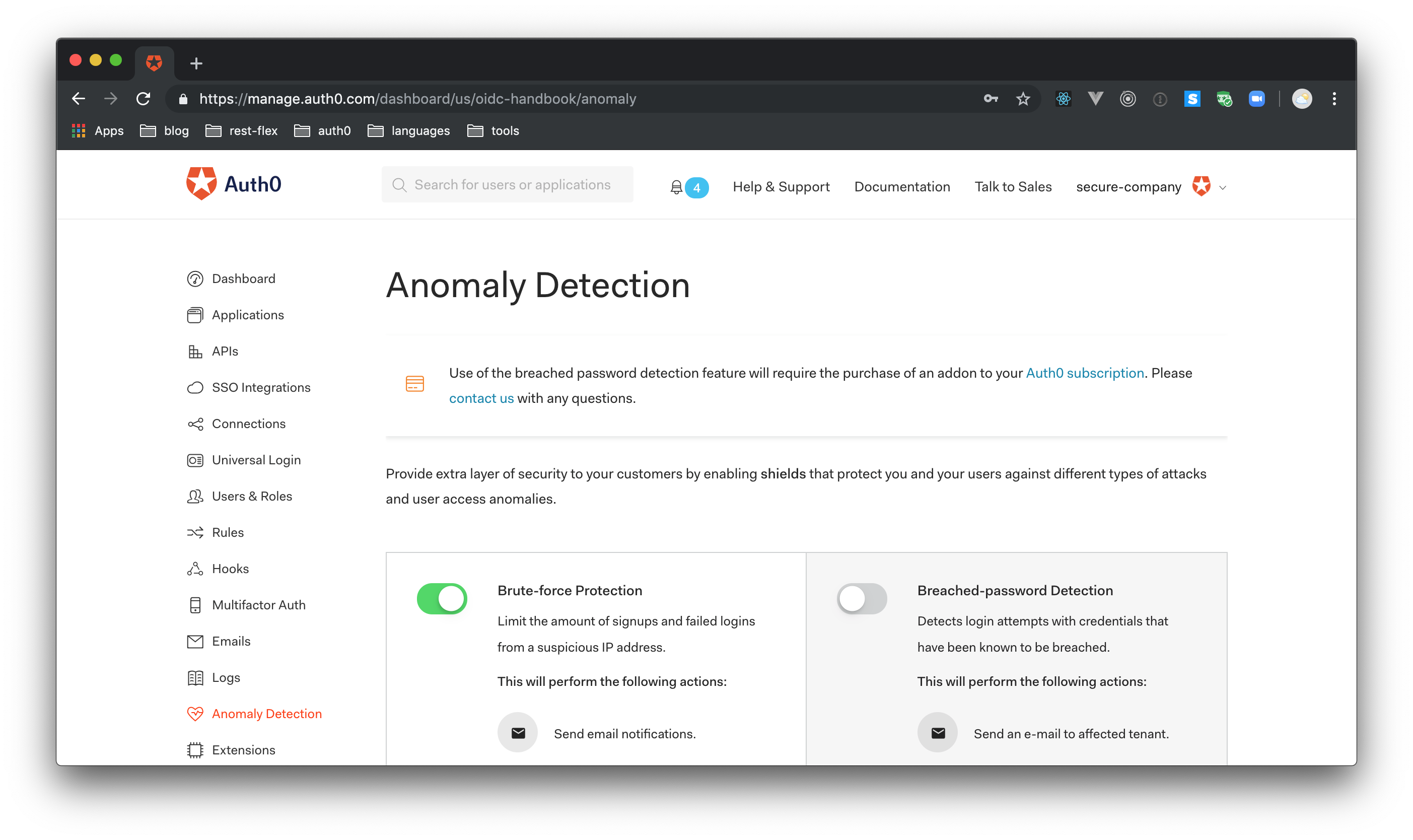
At a minimum, an effective enterprise mobility security strategy includes the ability to react swiftly to any flaws or mistakes. Auth0's anomaly detection and breached password detection can provide a backstop for your security plans. Anomaly detection spots suspicious behavior and breached password detection lets users know if someone has stolen and leaked their credentials.
A 2018 Ponemon study showed that a business with 10,000 compromised records or fewer lost an average total of $2.2 million. If a business had more than 50,000 compromised records, the average total cost reached $6.9 million.
Despite the danger of these breaches, the Ponemon study showed it takes 196 days, on average, to detect a breach. Absolute security is impossible, but your ability to react quickly can reduce the worst effects of a breach. Enterprise mobility strategies have to take account of the wide range of mobile security threats and develop plans to react to them.
Design Mobile Device Security Policies That Suit Your Use Cases
Security depends on internal policies that regularly educate employees and provides software infrastructure that makes those policies easy to follow. Every phase of a growing enterprise mobility strategy needs security policies.
The primary goal of a mobile device security policy is to assign and communicate clear responsibilities to different users. IT shouldn't bear the weight of security alone. Users across the company need to understand relevant security policies, and what they're responsible for handling.
Even if your organization is embracing BYOD, internal rules are still necessary to regulate how employees access data with their devices. Though BYOD appears simpler, EMM products enable IT to take more responsibility, such as configuring updates and patches.
Beyond regulating everyday user behavior, effective enterprise mobility policies isolate potential vulnerabilities and protect valuable data. IoT devices, including devices as mundane as wireless printers, should connect via a separate, isolated network, such as a virtual local-area network (LAN). IT should also disable unused functions to reduce vulnerabilities, especially ones that require network access.
Comprehensive policies also determine which data should be encrypted. Encryption ensures that a breach, if one were to happen, only exposes inscrutable data. Without the key — the ability to decode and understand the data — it's useless to a hacker.
Similarly, using multi-factor authentication (MFA) can make one set of credentials useless. Even if a user loses a password, you can still require a fingerprint or SMS code before granting full access.
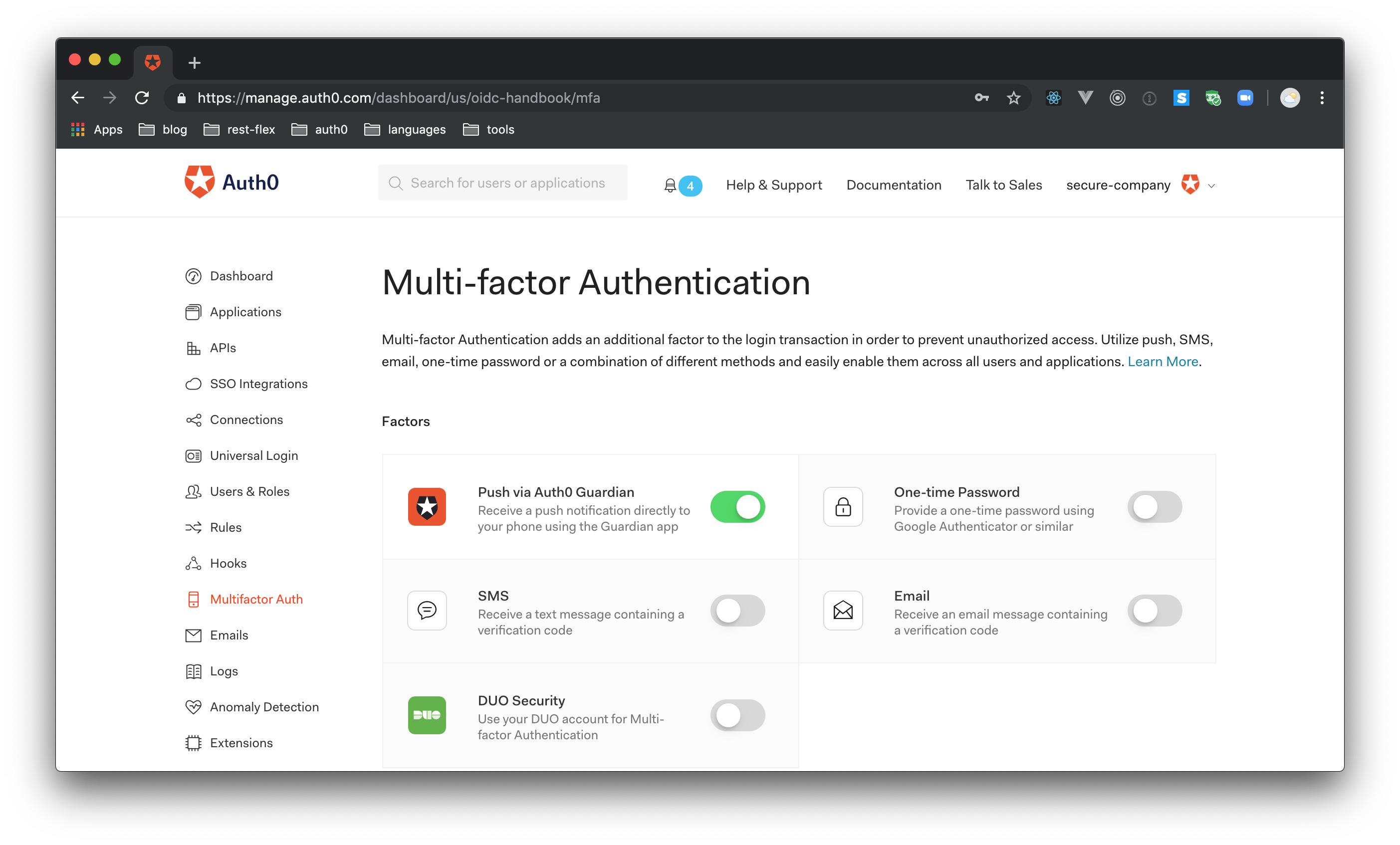
Enterprise mobility isn't exclusively about giving users flexibility. Products like Auth0's Guardian can approve login requests from a variety of devices. With MFA as part of your enterprise mobility strategy, you can turn mobility into a strength. The better you can manage security, the more freedom you can grant your users.
Build a Security Culture That Reinforces Mobile Device Security Best Practices
Mobile device security policies regulate user behavior from the top down, but an enterprise mobility strategy that prioritizes security isn't complete without bottom-up best practices.
Devices go inside and outside the office, connect to different networks, and interact with a variety of websites and applications. The best protection against the threats that mobility faces is a strong security culture, and an infrastructure to support it.
Culture consists of behaviors and practices you want to encourage and discourage. Asking people to participate in that culture means it's incumbent on you to explain those behaviors in terms that are real and relevant to the participants — your employees.
In many cases, you might not want employees to connect to public wi-fi networks. This is inconvenient — acknowledge that. Instead of admonishing or encouraging them, walk your employees through the threats public wi-fi networks pose. Show them how a seemingly innocent behavior can expose their data, their credentials, and potentially an enterprise-wide data breach. With the threat understood, employees can make better use of relatively easy solutions, such as using encrypted virtual private networks (VPNs).
The original tension between flexibility and manageability will remain a threat if your security culture consists exclusively of rules. Telling your employees to use different, complex passwords for every login reintroduces the friction that tempts employees to find workarounds.
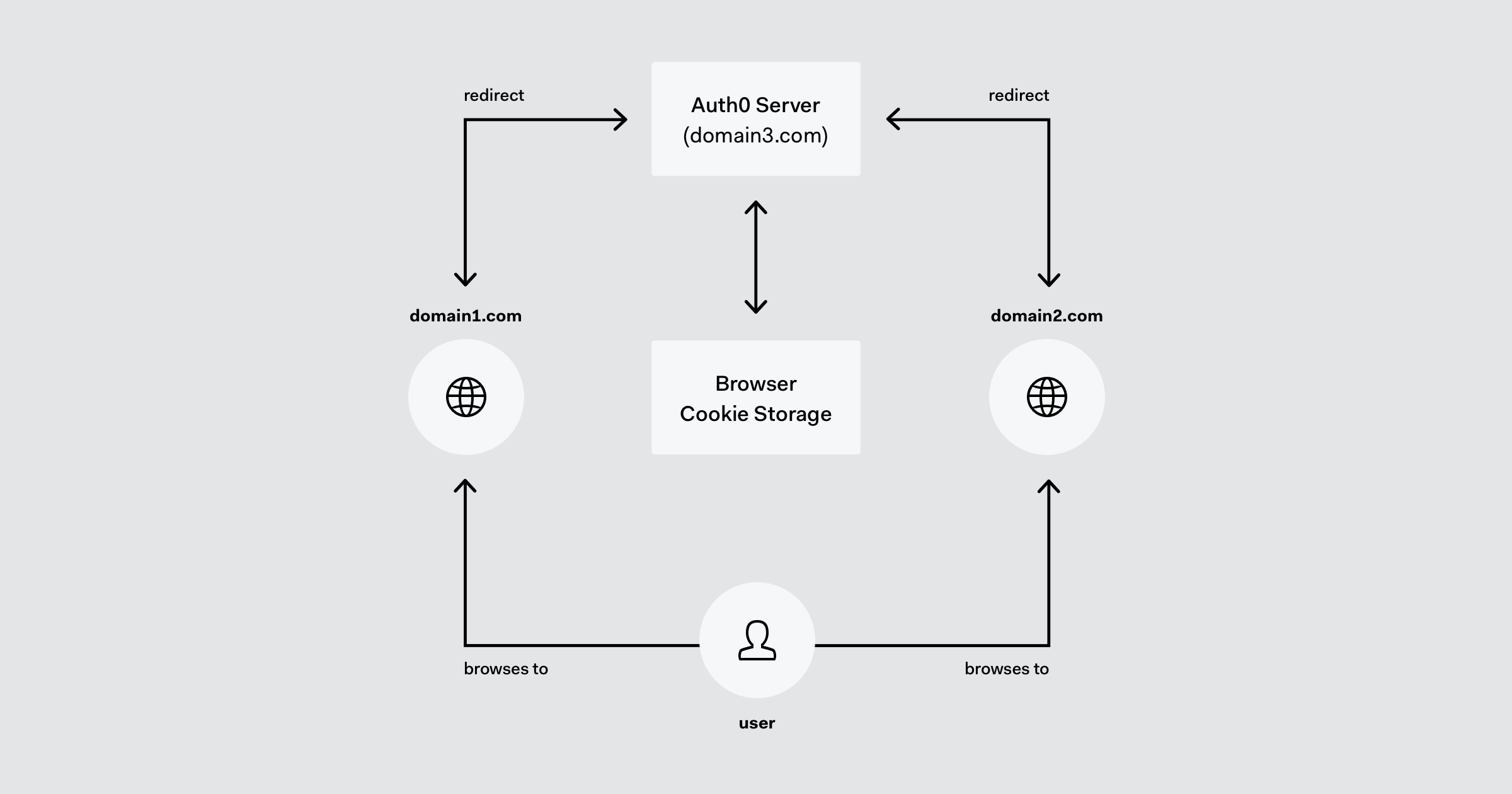
With enterprise single sign on (SSO), you can combine simplicity and security.
SSO uses a trusted, central server to process cookies. An employee's first login creates a cookie on the central server, so that when they need access to a second application, the central server can equip them with a token that keeps them logged in across applications.
Your users, and your security, benefit from simplicity. With security infrastructure, you can make security the more convenient option. Every time they use a tool like SSO, they're following a best practice and reinforcing the security culture that needs them.
Effective Enterprise Mobility Makes It Easy to Be Secure
Security can be a priority for your enterprise mobility strategy — no matter what stage your plans are in. Whether employees are bringing their own devices to work or logging into an EMM product, you can provide the infrastructure that makes security easy.
If your enterprise mobility strategy doesn't address that core conflict between freedom and manageability, expect security issues to crop up again.
Security and ease-of-use don't need to be in constant tension. If you enable your users to stay secure as you (or they) introduce new technologies and use cases, then your business strategies can be proactive, instead of reactive.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile