Many small business leaders believe their companies are safe from cybersecurity threats. In a 2017 study by Insureon, just 16% of 2,400 respondents were concerned about a cybersecurity attack — down from 18% the year prior.
Small business leaders assume their teams are too small to be worthwhile targets — or that existing IT teams can handle external threats. In particular, startup founders must juggle numerous other priorities as they scale, like getting to product-market fit, hiring, and fundraising. If cybersecurity isn’t front of mind, it’s less likely the team will make a concerted effort to improve their current infrastructure.
Yet this lack of attention can be a fatal mistake. Hacking operations often use bots to crawl multitudes of sites looking for known vulnerabilities. In these situations, company size doesn’t matter. While security disasters at massive companies, such as Anthem and Target, dominate headlines, startups, and the rest of the small-to-medium businesses often make easy prey because they devote fewer resources to defense.
How can small teams protect themselves when resources are low and other projects are vying for immediate attention? In this piece, we highlight three areas where startup and small business leaders can invest their time and money to secure their sensitive data and safely grow.
1. Secure your users from the start.
From the moment you begin hiring, safely and easily managing access to your technical systems becomes a challenge. Yet the pace of startup growth and the looming chance of failure can make it difficult to spend time on credential management.
A lack of a strong user management and authentication system, however, can sink you.
In Verizon's annual Data Breach Investigations report, they found that 63% of confirmed breaches involved weak, default, or stolen passwords. A bad password doesn't threaten a single account. If users reuse passwords, one compromised account could lead to the loss of many other devices and systems.
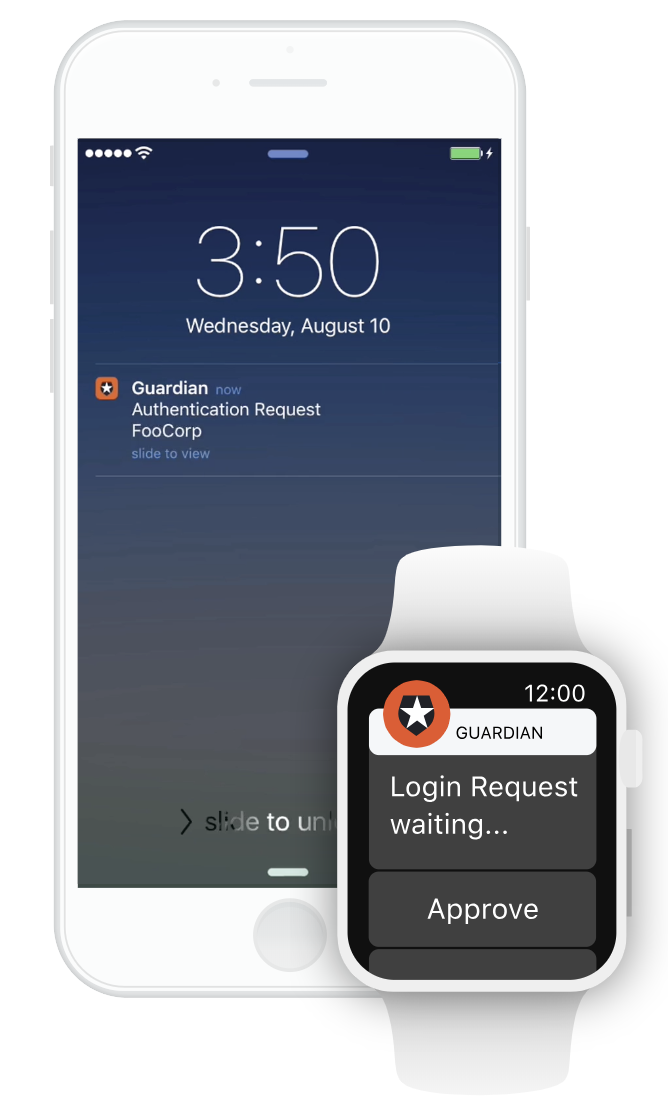
A solution like Auth0 provides multi-factor authentication (MFA) that bypasses password vulnerabilities and enables admins to immediately approve login requests with a single click across a range of devices.
With MFA in place, users need a second piece of sensitive information, such as a thumbprint or facial scan, to access other systems. Hackers with only one set of credentials can't get any further.
Auth0 Guardian helps startups keep moving by ridding employees of pesky, single-use login codes. With push notifications, busy admins can approve or deny requests without ever having to open the app. Guardian also offers mobile Software Development Kits (SDKs), so that you can design your own MFA application that integrates smoothly with the rest of your company's branding.
2. Plan your response to attacks.
Unfortunately, with data breaches on the rise, you can’t afford to not plan ahead.
In 2017, the startup Kickico found itself unprepared. They endured a wave of distributed denial-of-service (DDoS) attacks as hackers spoofed their site, cloned their platform on GitHub, and readied the clone to fool potential users once the original site went down. Luckily, the hackers appeared to run out of funds to keep up the DDoS attacks, and GitHub promptly responded to Kickico's request to block the attackers.
Kickico wasn't ready, and admitted “We did not realize such a small and inconspicuous company without huge PR actions [would] attract any attention.”
Many startups are ill-prepared and subtle attacks can take much longer to detect. One study found that over two-thirds of companies took months or longer to discover a breach—even though those breaches took mere minutes to accomplish.
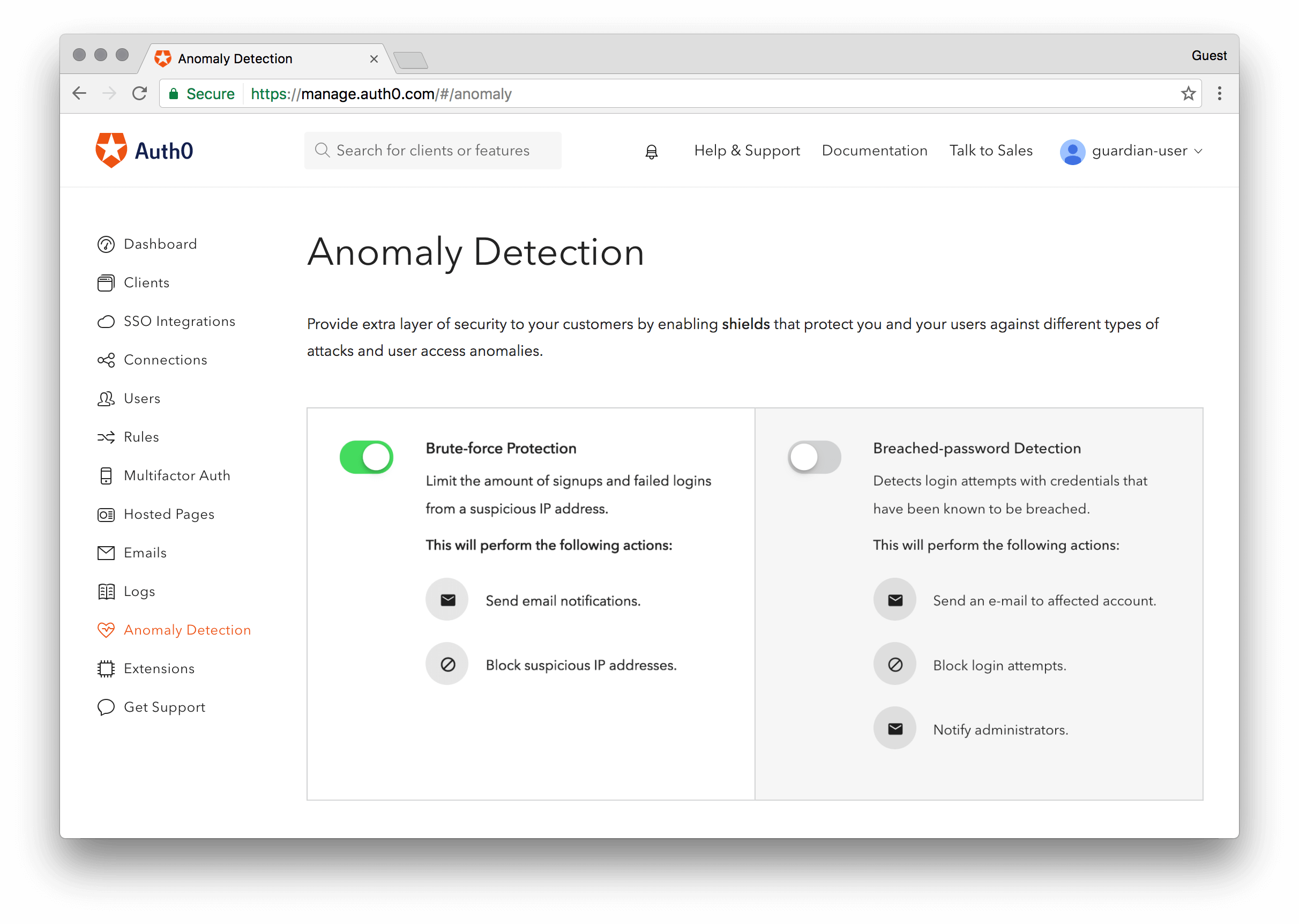
Startups can build in preparedness with tools that offer breached password notifications, so that you know about leaked credentials instantly, and can even lock out users until they reset their passwords.
With anomaly detection in place, startups can also set limits on brute force logins before they happen, establishing a baseline level of preparedness.
These cybersecurity best practices can buttress a data breach response plan, which prepares startups to react as quickly as possible to a breach. Rather than taking it alone, startups should form relationships early on with law, public relations, and incident response firms that are familiar with data breaches. Once you detect a breach, you can follow the plan and leverage the experts to recover as quickly and fully as possible.
Data privacy laws are also increasingly taking breaches more seriously, requiring faster responses and imposing stiffer penalties. A well-thought-out data breach response plan, informed by automatic detection, is only going to become more necessary.
“Many startups are ill-prepared to tackle cybersecurity attacks and subtle ones can take too long to be detected. One study found that over two-thirds of companies took months or longer to discover a breach.”
Tweet This
3. Guard against web-based attacks.
Your website is like your company's front door, yet hackers have thousands of ways in. Forty-nine percent of cyber attacks are web-based, and 44 attacks per day strike the average small business site.
Web security depends on more than the connection between two entities. Data goes through third parties to get where it needs to go, so authentication at all stages is central to secure communication.
If the right communication protocols aren't set, transmitted information can become vulnerable to so-called man-in-the-middle attacks. HTTP, an application protocol you've likely seen in many URLs, is historically focused on sending information, not securing it.
HTTPS, a newer protocol with security built in, makes attacks much harder to accomplish. HTTPS adds Transport Layer Security, or TLS, which ensures a client is only communicating with the expected server and that all data passed between is encrypted.
Using an HTTP Strict Transport Security, or HSTS, header reinforces HTTPS across your web application by telling browsers your site can only be accessed through HTTPS. Even if users have an older version bookmarked or type http://, an HSTS header forces browsers and applications to use HTTPS instead. Hackers won't be able to access the encrypted information, steal your site's cookies, or force a redirect to a spoofed site.
Auth0 enforces HTTPS connections to all of its services, which means any non-HTTPS connections will be upgraded.
Startups have to use their limited resources judiciously, but in the same way, a new restaurant wouldn't skimp on locks, neither should startups ignore these web security best practices.
Security on day one
Poor cybersecurity is technical debt. These shortcuts can keep a company moving but compound over time, eventually becoming expensive burdens. You can wait on establishing good cybersecurity procedures, but hackers won't. The longer you take to make security a priority, the harder it's going to be to retroactively protect yourself.
Cybersecurity is an investment in the sustainability of your company. Growth without cybersecurity best practices in place is growth for the benefit of hackers seeking a big payout.
Start by addressing one of your primary vulnerabilities: identity. With an outsourced provider like Auth0, you can scale security with user growth, form an informed threat response plan, and build a secure login environment. Investing in security early will keep you safer and better-informed when it matters most.
“Cybersecurity is an investment in the sustainability of your company. Growth without cybersecurity best practices in place is growth for the benefit of hackers seeking a big payout.”
Tweet This
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile