In today's rapidly evolving digital landscape, Software as a Service (SaaS) applications have become an integral part of numerous businesses worldwide. As these applications typically handle sensitive information, robust authentication mechanisms are crucial to ensuring the security and privacy of user data. The importance of authentication in SaaS applications cannot be overstated. It forms the first line of defense against unauthorized access, preventing data breaches and maintaining the trust of clients and end-users.
This article will dive into the pitfalls developers, indie hackers, and organizations often encounter while building or implementing authentication and authorization models.
Recognizing and addressing these issues can strengthen your SaaS application's authentication process, bolstering security and reducing the likelihood of cyber-attacks.
Allowing for Weak Passwords
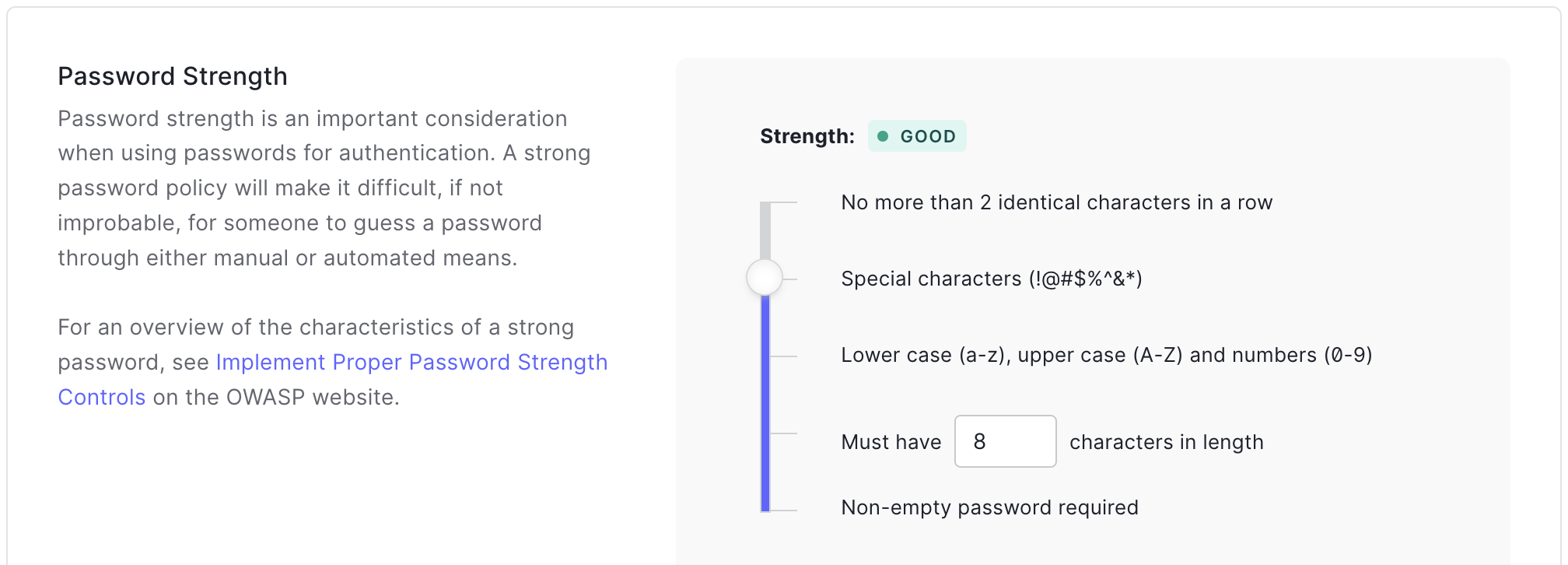
One common authentication mistake made in SaaS applications is permitting users to create weak passwords. You've likely encountered websites or apps that don't enforce strong password requirements, allowing users to set passwords like "123456" or "password." While allowing simple and easy-to-remember passwords might seem user-friendly, this approach poses a significant security risk.
Hackers can easily guess or crack weak passwords, making it simpler for them to gain unauthorized access to user accounts. Dealing with sensitive data in a SaaS application can lead to data breaches, loss of user trust, and even legal consequences.
Here's why allowing for weak passwords is a mistake and how you can promote the use of stronger passwords in your SaaS application:
- Enforce password complexity: Encourage users to create strong passwords by requiring a mix of uppercase and lowercase letters, numbers, and special characters. Implementing these requirements makes it more challenging for hackers to guess or brute-force passwords.
- Set a minimum password length: Longer passwords are generally more secure. Aim for a minimum password length of at least 10 characters, increasing the possible combinations and making it harder for attackers to crack passwords.
- Disallow common passwords: Numerous online lists contain the most commonly used passwords. Cross-checking user-created passwords against these lists can help prevent users from choosing overly simplistic or frequently used passwords. Implementing this measure adds an extra layer of security to your SaaS application.
Even when you can guarantee safe passwords, you should take additional measures when building or implementing your authentication system, like building a brute-force prevention mechanism that temporarily locks user accounts, IP addresses, or prompts for captchas.
The good news is that authentication platforms like Auth0 have your back! Auth0 offers a comprehensive solution that supports all these security measures and more right out of the box.
Try out the most powerful authentication platform for free.
Get started →Not Allowing for MFA (Multi-Factor Authentication)
Multi-factor authentication (MFA) is a crucial security measure that adds an extra layer of protection to the authentication process.
Despite its importance, many SaaS applications still do not support MFA, leaving user accounts more vulnerable to unauthorized access.
By neglecting to include MFA as part of your authentication strategy, you risk compromising the security of your users and your application.
Building and implementing an MFA solution is a daunting task due to its technical complexity and the challenge of balancing security with usability. First and foremost, there are multiple types of MFA, and not all MFA is created equal. There are different authenticators, factors, and levels of assurance, and which one you use will depend on your use case. Most teams don't have the necessary skills or resources to work on the task of building and implementing not one but many of these technologies and making them work seamlessly.
Here's why MFA is essential in your SaaS application:
- Enhanced security: MFA significantly reduces the likelihood of unauthorized access, requiring users to provide multiple independent factors to verify their identity, like entering a code sent via SMS or using a biometric. This makes it much more difficult for attackers to compromise accounts, even if they have managed to obtain a user's password.
- User trust: By demonstrating a commitment to security through the implementation of MFA, you can foster trust among your users. This trust is critical for retaining customers and attracting new ones, as users are more likely to choose SaaS applications that prioritize the protection of their data.
- Reduced risk of data breaches: MFA helps to minimize the risk of data breaches caused by compromised credentials. This not only protects your users' information but also safeguards your organization's reputation.
- Phishing and credential theft protection: MFA can help protect your users from phishing attacks and credential theft. Even if a user's password is compromised, an attacker would still need to bypass the additional authentication factors, making it much more challenging to gain unauthorized access.
Overlooking Social Engineering Attacks
Social engineering attacks, which exploit human psychology to manipulate individuals into revealing sensitive information or granting unauthorized access, are often overlooked when it comes to securing SaaS applications. These attacks can be particularly dangerous, as they bypass traditional security measures and target the weakest link in the security chain – the human element. Failing to address social engineering risks can leave your SaaS application vulnerable to data breaches, unauthorized access, and reputational damage.
Social engineering attacks come in various forms, each designed to manipulate individuals into divulging sensitive information or granting unauthorized access. Some common examples of social engineering attacks include:
- Phishing: Phishing attacks involve sending fraudulent emails or messages that appear to be from a legitimate source, such as a bank, a popular online service, or a colleague. These messages typically entice victims to click on malicious links, download harmful attachments, or provide sensitive information, such as login credentials.
- Spear phishing: A more targeted form of phishing, spear phishing involves crafting personalized emails or messages for specific individuals or organizations. Attackers research their targets and use this information to create highly convincing messages, increasing the likelihood of a successful attack.
- Pretexting: Pretexting is a social engineering attack in which the attacker creates a fabricated scenario or identity to manipulate victims into divulging sensitive information or granting access to restricted resources. This may involve impersonating a co-worker, a client, or an authority figure, such as a company executive or a law enforcement officer.
- Baiting: Baiting involves enticing victims with a seemingly valuable item, such as a free USB drive or a downloadable file, that contains malicious software. Once the victim takes the bait and accesses the resource, the attacker can gain control of the device or obtain sensitive information.
There are many more forms of attacks, and bad actors are coming up with new, smarter ways to get access to your systems and steal or manipulate valuable information.
There are multiple strategies and best practices to prevent these bad actors from gaining complete access to your systems. Here are some recommendations for your SaaS applications:
- Raise awareness and regular training: Educate your users, employees, and development team about the various types of social engineering attacks, such as phishing, pretexting, and baiting. By increasing their awareness, they will be better prepared to recognize and avoid falling victim to these tactics.
- Implement MFA: As mentioned earlier, multi-factor authentication (MFA) adds an additional layer of security to the authentication process. Even if a social engineering attack succeeds in obtaining a user's password, MFA can still help prevent unauthorized access by requiring additional verification.
- Develop clear communication policies: Establish and communicate clear policies regarding how your organization handles sensitive information. For example, specify that employees should never share passwords or personal information through email or over the phone. Make sure that all employees understand these policies and know to question any requests that seem suspicious or violate established protocols.
- Implement robust access controls: Establish strict access controls to ensure that users only have access to the information and resources necessary for their roles. By minimizing the number of individuals with access to sensitive data, you can reduce the potential damage caused by successful social engineering attacks. For example, use robust and adequate authorization models for your systems and follow the principle of Least Privilege Access
- Monitor and respond to suspicious activity: Implement monitoring systems to detect and alert your security team of any unusual or suspicious activity within your SaaS application. Timely detection and response can help mitigate the impact of a social engineering attack and prevent further damage.
- Regularly review and update security measures: Continuously assess your SaaS application's security measures, and make updates as needed to stay ahead of evolving threats. By regularly reviewing and updating your security protocols, you can better protect your application from social engineering attacks.
- Encourage reporting: Create a supportive environment where users and employees feel comfortable reporting any suspicious activity or potential social engineering attempts. Encourage open communication and ensure that they know how to report incidents without fear of reprisal.
Not Implementing Appropriate Authorization Model
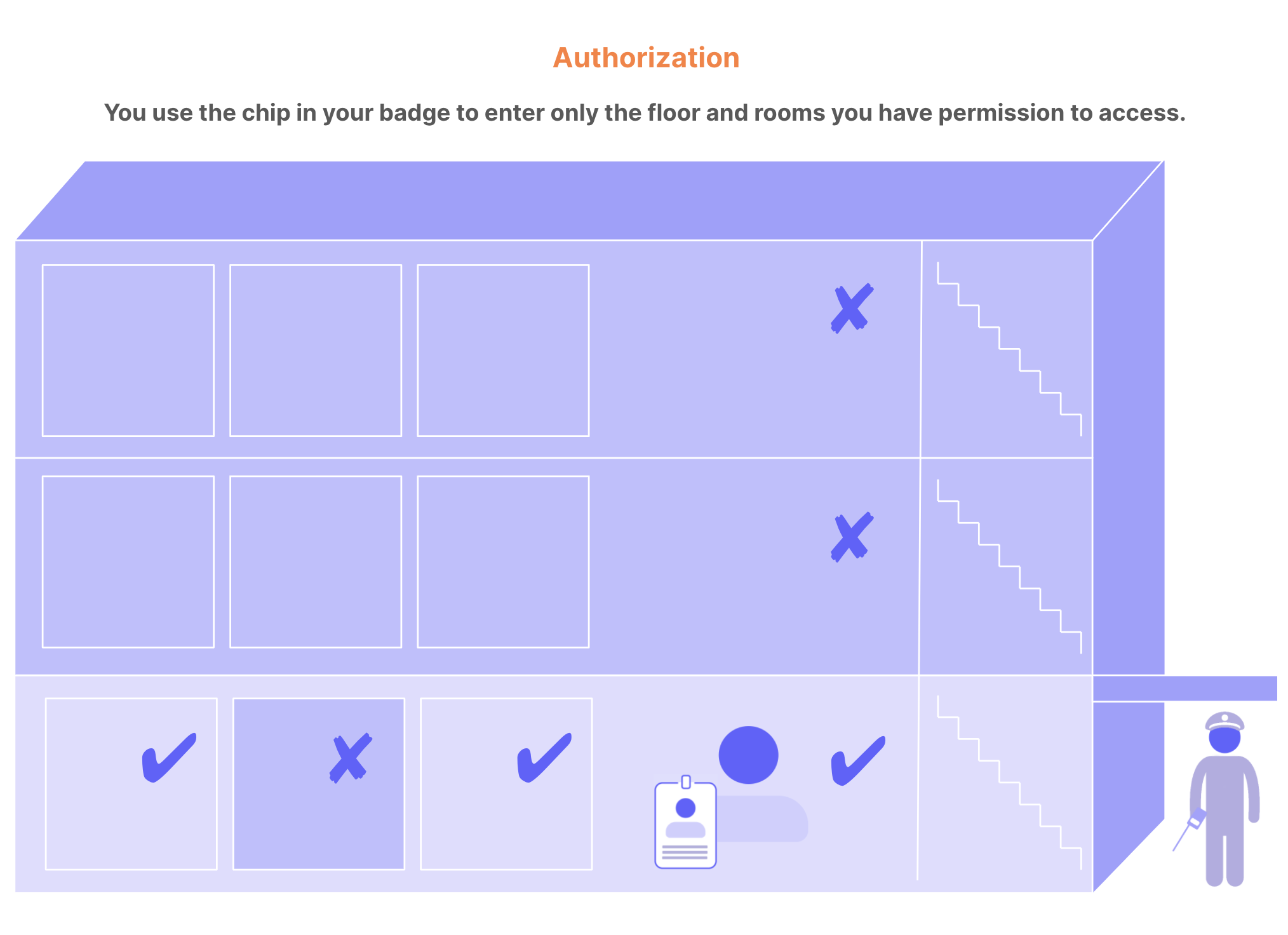
Authorization is the process of verifying what a user has access to. In SaaS applications, implementing an appropriate authorization model is crucial to ensure that users can access only the resources and functionalities they are authorized to use.
Implementing authorization models in SaaS applications provides several benefits, including:
- Improved security: Authorization models ensure that only authorized users can access sensitive data or perform specific actions. This minimizes the risk of data breaches, insider threats, and unauthorized access, protecting both the application and its users.
- Enhanced compliance: Authorization models can help ensure that your application meets compliance requirements, such as HIPAA, GDPR, or PCI DSS. By using RBAC or other authorization models, you can control access to sensitive data and demonstrate that you have appropriate safeguards in place.
- Greater flexibility: Authorization models allow you to grant different levels of access to different users or groups, providing greater flexibility in managing your application's security. This flexibility allows you to adjust access permissions as user roles or job functions change, ensuring that users only have the access they need.
There are several types of authorization models that can be used in SaaS applications, including:
- Role-Based Access Control (RBAC): This is a hierarchical system of roles that define what actions can be taken within the application. Users are then assigned to roles based on their job function or level of access required. This is one of the most commonly used authorization models in SaaS applications.
- Attribute-Based Access Control (ABAC): ABAC is a more flexible authorization model that allows access decisions to be based on a combination of user attributes, such as job title, department, or location. This provides greater granularity in access control but can be more complex to implement and manage.
- Rule-Based Access Control (RuBAC): This authorization model uses rules to determine access rather than roles. Rules can be based on a variety of factors, such as time of day, IP address, or device type.
- Mandatory Access Control (MAC): MAC is a more restrictive authorization model that uses a set of predefined rules to determine access. This is often used in high-security environments, such as government or military applications.
- ReBAC (Relationship-Based Access Control): ReBAC is an emerging authorization model that is designed to manage complex relationships between users and resources. It takes into account factors such as ownership, location, and context to determine access, and it helps solve the most critical API security risk.
When implementing an authorization model, it's important to consider the specific needs of your application and user base. RBAC is a common choice for many SaaS applications, as it provides a straightforward and hierarchical way to manage user access.
Overall, the choice of authorization model will depend on the specific needs of your application, as well as the complexity of your user base and resource hierarchy. It's important to carefully consider your options and choose an authorization model that balances security, manageability, and usability.
 Want to take your Authorization to the next level? → fga.dev
Want to take your Authorization to the next level? → fga.devBuilding Your Own Authentication and Authorization Module

As a SaaS application developer, you're responsible for ensuring that your application is secure, reliable, and compliant with industry and regulatory standards. Authentication and authorization are critical components of your application's security, allowing you to control user access and protect sensitive data from unauthorized access.
But, as we covered so far, building an authentication and authorization module is not as trivial as a username and password form; there are a lot of complexities that arise like safely storing sensitive information such as passwords, implementing MFA in its multiple forms, building brute force protection, monitoring systems, and much more.
Furthermore, building your own authentication and authorization module can lead to significant security vulnerabilities, performance issues, and compliance problems. It requires expertise in security and cryptography and can be time-consuming and resource-intensive. Additionally, building your own module can lead to limited functionality and features and requires ongoing maintenance and support.
Fortunately, there's a solution to this problem: leveraging existing authentication and authorization solutions. These solutions have been rigorously tested and proven to provide secure and reliable authentication and authorization functionality, allowing you to focus on building your application and providing value to your users.
Auth0 is a cloud-based identity platform that provides secure authentication and authorization functionality, as well as a range of other features, such as social login, multi-factor authentication, and identity federation. With Auth0, you can easily integrate authentication and authorization into your SaaS application without the need for complex custom development.
Using Auth0 can provide several benefits for your SaaS application, including improved security, simplified access management, and enhanced compliance. Additionally, Auth0 offers dedicated support teams and ongoing updates to address security vulnerabilities and compliance issues, reducing the burden of ongoing maintenance and support.
If you're interested in trying Auth0 for your SaaS application, you can sign up for a free Auth0 account. With a free account, you can explore the features and functionality of Auth0 and determine if it's the right solution for your application. So why not give it a try and see how Auth0 can help improve the security and performance of your SaaS application today?
Thanks for reading!
About the author

Juan Cruz Martinez
Staff Developer Advocate

