The National Institute of Standards and Technology (NIST) sets the rules that govern the protection of digital identities for federal agencies in the United States — yet NIST policies can also be secret weapons for other organizations striving to stay on the front lines of digital security.
If you’re tasked with organizing and processing sensitive data for your team, you can’t afford to ignore the new 2019 NIST Privacy Framework draft.
More than a policy to simply adhere to, the Privacy Framework, which builds on the widely adopted NIST Cybersecurity Framework, includes important takeaways that can help your organization meet its cybersecurity needs more efficiently and effectively (and free your technical talent up for projects that clearly drive ROI).
NIST emphasizes how important it is not to treat user privacy as an externality — a risk that’s isolated from your core operation, to be treated independently (e.g., after a data breach). Instead, NIST helps you build privacy into the design of your organization. This can significantly reduce the risk of data loss and data breaches — and can help teams scale with a more sustainable foundation.
Before you wade through the full text of the NIST Privacy Framework draft, this piece digs into its fundamentals, highlights important differences from the Cybersecurity Framework, and offers suggestions for using the Privacy Framework to shape a more stable and successful business.
How To Approach the NIST Privacy Framework
To realize the value of the NIST Privacy Framework, it’s important to understand its current structure.
The NIST Privacy Framework has three major parts: the Core, the Profile, and the Implementation Tiers.
- Core: A set of activities and outcomes that you use to communicate privacy priorities across your organization. You can use your Core to quickly communicate and plan your privacy risk strategy.
- Profile: The privacy outcomes you want to achieve, which you can select from the Privacy Framework and tailor to your needs. You can design a current Profile that identifies your current state, and build toward a target Profile that identifies your goals.
- Implementation Tiers: The kinds of approaches you can take to meet your goals. NIST provides a spectrum, from reactive responses to agile strategies.
If you’re not a U.S. federal agency, NIST doesn’t require strict compliance. Instead, it serves as a comprehensive resource to support organizations in making more informed and valuable decisions about privacy.
As with its Cybersecurity Framework, NIST writes flexibility into its privacy guidelines, encouraging readers to customize its principles to their specific business and industry. It’s up to each team to tailor NIST approaches to achieve their desired outcomes.
Below are five key takeaways from the 2019 NIST Privacy Framework draft that can support teams as they scale.
1. Distinguish between cybersecurity and privacy to create a more powerful platform
Although the Privacy Framework shares several goals and tools with the Cybersecurity Framework, NIST created it as a standalone document for good reason. In 2018, Ponemon found that internal issues of data privacy (including system glitches, human error or negligence) cost companies a combined $259 per record to resolve — in contrast with the cost of an outside cybersecurity incident at $157 per record.
Cybersecurity procedures go a long way toward protecting data from unauthorized activity, but privacy risks are increasingly embedded in a system’s architecture. They arise from the regular, authorized data processing and analyses that teams undertake on an ongoing basis to achieve their mission and set and hit their KPIs.
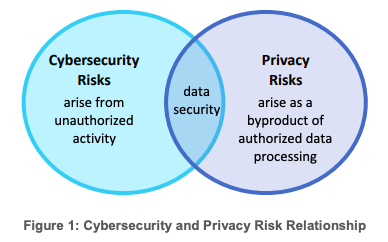
For teams looking for the most powerful and precise ways to protect their data, distinguishing between the two — and giving weight to each — is essential.
To this end, NIST suggests creating separate privacy policies that specifically address data processing. This can go a long way towards reducing errors on the part of authorized employees, negative consequences for customers, and adverse impacts on company health.
2. Build systems that enable you to control data (and harness it to your advantage)
Controlling sensitive data, such as user credentials or customers’ financial information, is imperative for any team today. Yet, as your team’s information grows in volume and becomes more complex, it can be a challenge to set clear policies on how to do this. Moreover, data control can create tension within a team. Since data is often spread throughout a company, data control often requires input from several departments, each of whom may be used to setting up and executing on their policies independently.
To help streamline the process, NIST pushes for greater transparency about privacy practices — which many companies lack. According to NIST, it’s common to bolster privacy by way of obscurity. This includes scheduling data for automatic deletion or using cryptographic techniques that make it hard for the organization itself to access data. Obscurity might grant a degree of privacy, but it also limits your ability to keep your users informed and respond proactively.
A solution like Auth0’s Dashboard can help you open up this process. Team members can view (in real-time and historically) who is accessing and working with data sets.
In addition, it’s simple for Dashboard admins to manage privileges of user accounts and configure it for any given tenant. This clarity and ease-of-use reduces risk of data loss, ensuring only those who should have privileges to move or manipulate the information do.
While many sections in the Privacy Framework draft are lifted from NIST’s prior Cybersecurity Framework, its emphasis on keeping everyone on a team informed about data control and data privacy processes is new.
According to NIST, it’s critical to make this information available and digestible to its employees. Doing so helps builds accountability within an organization. In the event of a systems breach or data loss, for example, it becomes clear who was responsible for keeping the information secure. In addition, it helps expose vulnerabilities that a team can move swiftly to fix.
3. Think on an industry level to create comprehensive privacy policies
When it comes to data, the amount of intermediaries between businesses and their users can be dizzying. A single organization might use multiple cloud services for storage, several customer intelligence tools to inform outreach, and numerous data analysis tools to shape user onboarding.
Even a simple landing page might rely on traffic from Facebook ads, user feedback from Hotjar, email address collection from Mailchimp, and on-demand server elasticity from Amazon Web Services (AWS).
NIST drives home that agencies must consider these external relationships when developing their privacy policies — or risk data exposure on a regular basis. Moreover, NIST wants teams to think beyond what information they might share with their partners and conceptualize risk management in their industry more broadly.
For example, one business might be a service provider to other businesses, offer products to individual customers, and work with regulatory organizations. Privacy-focused teams have to think up and down the stack, considering privacy needs and requirements across a web of stakeholders, as NIST depicts in the figure below.
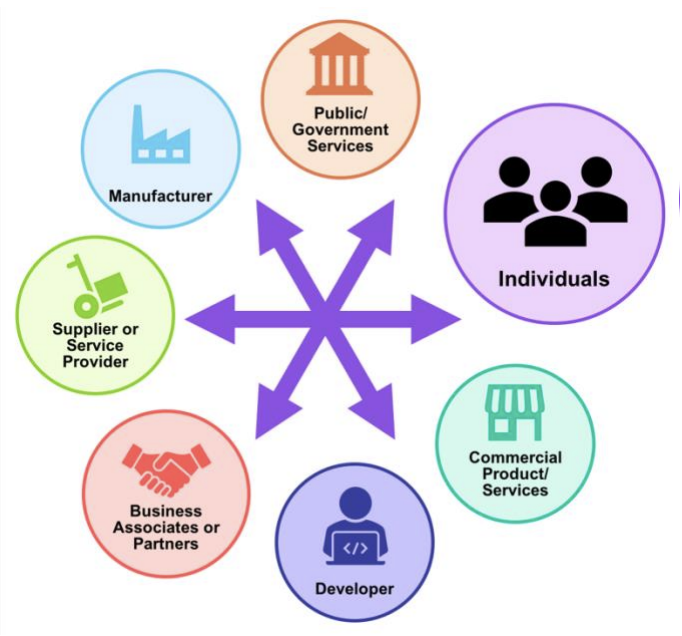
Business leaders can use NIST’s recommendations to determine the privacy requirements they want from partners and write contracts that codify and enforce them. To solidify these requirements, NIST recommends communicating about them with third parties regularly, showing partners how you’ll verify and validate them.
4. Design response plans to reduce reputational damage
The scale and precision with which hackers now operate mean every organization needs to plan for a hack or breach — no matter their size or how comprehensive their current security systems. Even startups just beginning to capture and store user data have to keep this front of mind.
In addition, a response plan must be deliberate and thorough. According to NIST, response plans should involve internal and external stakeholders, such as law enforcement and lawyers specializing in cybersecurity. NIST strongly suggests including notification systems that enable teams to move quickly to mitigate and contain privacy problems.
This can be a daunting task for any security team — yet the faster and more accurately you can respond, the more impressive you will appear to your users. In 2018 Ponemon found the teams with clear incident response (IR) protocol were able to reduce the cost of a data breach by $14 per compromised record — resulting in an adjusted cost of $134/record v. $148/record. Multiplied by thousands or even millions of users, this cost savings quickly adds up.
On the flip side, if you’re slow and opaque, you could quickly lose your customers’ trust — and be subject to additional fines. For example, the California Consumer Privacy Act (CCPA) will institute fines of up to $7,500 for each privacy violation. In addition, the CCPA allows individuals to sue for any breach of their “non-encrypted or non-redacted personal information” — whether or not they incurred damages.
Privacy issues can be extremely complex, but your response doesn’t have to be. For example, implementing a tool like Auth0’s breached password notification can afford you the insight you need to immediately detect threats — and ability to take action. If a user’s password is leaked or stolen as a result of a data breach, Auth0 will notify you immediately. Once you’re informed, you can also inform your users. This underscores your skills and reinforces how much you care about those you work with.
5. Prioritize identity management to scale without fear
The NIST Privacy Framework places a special emphasis on identity management. If your business involves processing data, then the ability to authenticate and authorize access to the right individuals is fundamental.
According to NIST, organizations should be able to issue, manage, verify, revoke, and audit credentials as necessary. “Protect,” one of five functions in the NIST Privacy Framework’s Core, emphasizes the infrastructure that enables identity management, authentication, and data security.
Implementing granular user management, especially at scale, can be very complex. Even at the behest of NIST, it’s difficult for many organizations to allocate adequate resources to build an identity management system that serves their current needs — and is flexible enough to grow with them.
As you bring on partners, develop mobile apps or APIs, grow your user bases, or enter regulated industries, you might find you have to keep rebuilding your system. For this reason, businesses that want to get up to speed on identity, and remain at speed, often choose to buy rather than build their identity infrastructure. Partnering with identity experts like Auth0, focused exclusively on these solutions 24/7, can give you peace of mind and more leeway to create and refine your core products.
Make Privacy a Core Concern
NIST Frameworks are best together. Both the Cybersecurity Framework and the Privacy Framework can inform your approach to security, privacy, and risk management.
In particular, the NIST Privacy Framework enables businesses of all sizes to make privacy a priority. Rising public concern about privacy means that if businesses truly want to put customers first, they need to figure out how to put privacy front and center. NIST lays out a variety of tools you can use to build a path toward being a privacy leader.
The current draft is available online, and if you have feedback, you can contact NIST. As it did with the Cybersecurity Framework, NIST is currently gathering feedback from privacy and security specialists and expects to release a final version by October 2019.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile