Biometric authentication is a cybersecurity process that verifies a user’s identity using their unique biological characteristics as their password. By comparing a user’s biometric signature against one submitted and stored in a database, biometric authentication systems are able to determine whether the person is attempting to log in/access data/etc. Is actually who they say they are.
Biometric authentication is a rapidly evolving technology that can — if implemented correctly — help your business ensure that only the right people have access to sensitive information. Here’s what you need to know about biometric authentication as it’s used today, as well as what to be aware of for 2021 (and beyond).
The Benefits and Risks of Biometric Authentication
Biometric authentication is highly effective for securing data and other sensitive information because of the uniqueness of biometric characteristics.
Not surprisingly, Spiceworks found that 62% of the enterprises they surveyed in 2018 were already using it (with an additional 24% planning to implement it in the next two years:
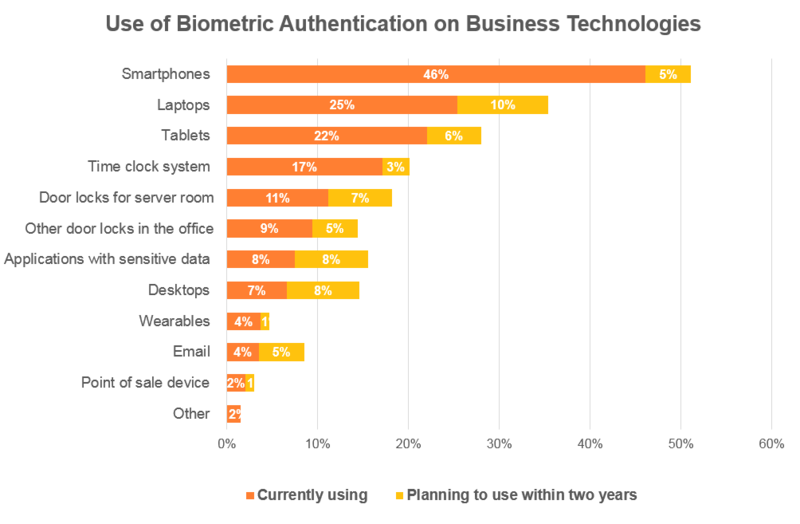
However, even as many businesses are moved to adopt biometric authentication, it’s important to note that it’s far from bulletproof.
Biometric authentication sensors can be costly to implement and aren’t always 100% secure. For example, when Apple first released TouchID in 2013, hackers cracked it in 48 hours. Even facial recognition, which can be costly to implement, isn’t that accurate.
Furthermore, biometric data can’t be “reset,” as a password can. Once biometric data is breached, it’s breached forever, which means that companies must be extra diligent in how that data is stored if they’re planning to utilize it to secure sensitive systems, locations, or information (more on this a bit later).
6 Common Types of Biometric Authentication Technologies
There are a number of biometric authentication systems in use today, with several that are still currently being researched for wider implementation. Here are the current and emerging technologies that you need to be aware of and how they’re currently used today.
Existing Biometric Technologies
Some of the biometric authentication technologies below are ones that you might use daily. Others may be less common (or less obvious). Below are the four most common use cases for biometric authentication technology in today’s world:
- Fingerprint Recognition: Fingerprint authentication uses a person’s unique fingerprint to verify their identity. It’s one of the most widespread biometric authentication technologies and is used to secure everything from mobile devices to automobiles and even buildings. Cheap fingerprint scanners can cost as little as $50.
- Face Recognition: Facial recognition systems use a person’s unique facial anatomy to identify them. It’s used in a variety of places, such as smartphones, identity verification for credit card payments, law enforcement, and is even used to purchase fried chicken in China.
- Retina/Iris Recognition: Retina or iris recognition uses the unique pattern of someone’s iris or retina to identify them. This type of biometric authentication is harder to implement (and therefore less common) because an iris scan requires an infrared light source, a camera that can see IR, and minimal light pollution in order to ensure accuracy. However, it is one of the most accurate biometric authentication systems available when those conditions are met. So it’s typically used in situations where security is most critical (nuclear research facilities, for instance).
- Voice Biometry: Voice biometry (or voice recognition implemented for cybersecurity purposes) uses the unique tone, pitch, and frequencies of someone’s voice to authenticate them. Today, this is most commonly used to verify users when they contact a call center for customer service support (online banking, for example).
Emerging Biometric Technologies
The two biometric authentication methods below aren’t as widespread yet, but they are well on their way to becoming more common:
- Gait Recognition: Gait recognition uses the way someone walks to identify them. Since each person walks a little differently, the way they put one foot in front of another is an effective way to verify their identity. We expect gait recognition (and other technologies like it) to become more common in the future as forms of continuous authentication become more popular (more on this trend below).
- Vein Recognition: Vein recognition uses the unique pattern of blood vessels in a person’s hand (or their finger) to identify them. It uses infrared light to map the veins under the skin in your hands or fingers. Vein recognition is extremely accurate (more so than retina/iris) and one of the most cutting-edge biometric identification systems today.
Biometric Authentication Trends for 2021
While many companies have started incorporating biometrics into their security measures, the full scope of implementation is constantly growing and morphing (as are the security risks involved with doing so). Here are the trends to be aware of for 2021 and beyond.
1. Continuous biometric security improvement is a must
Even though biometric authentication is considered more secure than traditional passwords, hackers are always looking for (and finding) new ways to crack biometric authentication systems. So if you implement them to secure your systems or data, it’s important that you always improve your authentication security to match new threats.
Mastercard’s Identity Check Mobile (frequently referred to as “Selfie Pay”) is a great example of why continuous improvement is so critical. Users originally confirmed an online payment by snapping a selfie in the Mastercard app, and it used facial recognition software to verify their identity:
However, Mastercard figured out that you could easily bypass this process simply by holding up a static photo of someone’s face. So the company took things a step further and started requiring users to blink to confirm it really was their face in the frame. That small change made it far more difficult to fraudulently circumnavigate the authentication process.
Even the most secure biometric authentication measures have gaps ( for example, researchers were able to create a wax hand that easily bypassed vein authentication scanners). So if you’re going to utilize biometrics, it’s important to find these gaps (and plug them) before cybercriminals do.
2. Continuous Biometric authentication will continue to gain traction
Continuous authentication refers to authentication that happens on a rolling basis (and locks you out when the criteria for validation are no longer met). Many security experts expect biometrics to be more widely incorporated into continuous authentication processes as the zero-trust mindset becomes the norm across the cybersecurity industry.
Predominantly because continuous authentication creates a better user experience and because users prefer to use biometric authentication systems rather than passwords.
Continuous authentication is typically achieved by calculating an “authentication score” in real time that reflects the likelihood that a user is who they say they are. For example, some modern cars already use continuous authentication with their key fobs. When you walk away from certain cars with the key fob in your pocket, the doors lock, and the car will no longer start. And when you return, the car will often unlock itself on your arrival.
This ensures that only the person with the key fob (which should be an authorized user unless the key is stolen) has access. However, incorporating biometric identifiers (like a person’s gait or face) or behavioral characteristics (data from an app, for instance) into the key fob would add another layer of assurance that the person using a device or piece of software is still who they say they are.
“Biometric data can’t be “reset,” as a password can. Once biometric data is breached, it’s breached forever.”
Tweet This
That way, if the person’s gait were incorrect as they walked up to the car, the car could secure itself because it would know that the wrong person had the key fob.
3. Regulations around biometric data are tightening
Biometric authentication is still a relatively new technology, and current regulations around them are very much a work in progress. However, given the sensitive (and permanent) nature of biometric data, many regulators are quickly moving to firm up legislation on how that data is collected and stored.
For example, Illinois has been a leader in biometric data privacy since they first enacted the Illinois Biometric Information Privacy Act in 2008, which grants users a “property interest” in the algorithms that are used to establish their digital identities.
But the Illinois Supreme Court took this a step further in 2019 and ruled that private companies could no longer collect biometric data, including fingerprints, iris scans, and facial scans, from individuals without their consent (probably because there have already been over 100 suits filed about alleged violations of this law).
A number of other states, including Texas and Washington, followed in Illinois’ footsteps, implementing more comprehensive legislation around biometric data security in 2019 as well. It’s likely that the remaining states could quickly follow suit.
So it’s increasingly important for companies who use biometric authentication systems to stay up to speed on national, state, and industry regulations to ensure that they’re in compliance moving forward.
Biometric Authentication Is the Future
A survey conducted by Visa found that 86% of consumers actually wanted to use biometrics rather than traditional passwords to verify their identity. And although authentication using biometric characteristics is far more secure than relying on passwords alone, it’s also far from impenetrable. So companies have to stay ahead of the curve to ensure security.
If you’re overwhelmed by introducing biometrics for your own authentication processes, working with a trusted platform can help. Outsourcing a portion — or all — of your identity management can give you peace of mind, knowing you have an expert team dedicated to authentication 24/7.
Auth0 makes it easy to use biometrics for multifactor authentication (MFA). We’re here to help with any questions you may have about implementing it for your business. Get in touch!
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Diego Poza
Sr Manager, Developer Advocacy
