Time flies when you are having fun. It's December already and we are getting ready to wrap up this year. 2018 was a prolific year for the Auth0 blog: we published more than 200 posts (😱) where we tackled a diverse amount of topics: frontend and backend technologies, data breaches, GDPR, Cybersecurity, Company Culture, and of course, Identity.
We believe looking back is key to look ahead. That is why this week, we are going to take a look back at the best and most impactful posts we have published in 2018.
One article wouldn't be enough to review this amazing year, that's why we have decided to split this year in review into 3 parts: Developer Posts, Security Posts, and Identity Posts.
Without much further ado, here's the roundup of our 10 most-popular Identity posts this year!
Auth0's 10 Most-Popular Identity Posts in 2018
The following posts are not listed in any particular order.
- An Overview of Open Standards
- 3 IAM Examples to Support Digital Transformation
- A Look at The Draft for JWT Best Current Practices
- Introduction to Web Authentication: The New W3C Spec
- How To Have a Successful IDM Project
- How To Have a Successful IDM Project (Part 2)
- On The Nature of OAuth2’s Scopes
- Hashing Passwords: One-Way Road to Security
- Adding Salt to Hashing: A Better Way to Store Passwords
- How Utilities Can Use CIAM to Avoid 3 Common Problems
1. An Overview of Open Standards
In this overview, we will go over what open standards are and why they matter. We will also go over the top open standards used for identity including OAuth 2, OpenID Connect, JWT, and SAML. Open standards are important to understand but one can easily get overwhelmed by the technical specifications.
2. 3 IAM Examples to Support Digital Transformation
From basic website authentication to implementing an OpenID Connect server and API authentication: This article covers 3 IAM examples to support your Digital Transformation.
3. A Look at The Draft for JWT Best Current Practices
In this post, we will take a look at the draft for the JWT Best Current Practices document. This document describes common pitfalls and attacks related to the use of JWTs, and how to implement mitigations against them. Read on!
4. Introduction to Web Authentication: The New W3C Spec
Web Authentication brings a stronger authentication mechanism to the masses by defining an API that both authenticators and web browsers can implement. Learn why Google, Paypal, Mozilla, and others back it up.
5. How To Have a Successful IDM Project
Learn how to create a realistic project plan to have a good Identity Management project deployment.
6. How To Have a Successful IDM Project (Part 2)
Learn how to plan for failures and changes in your identity project.
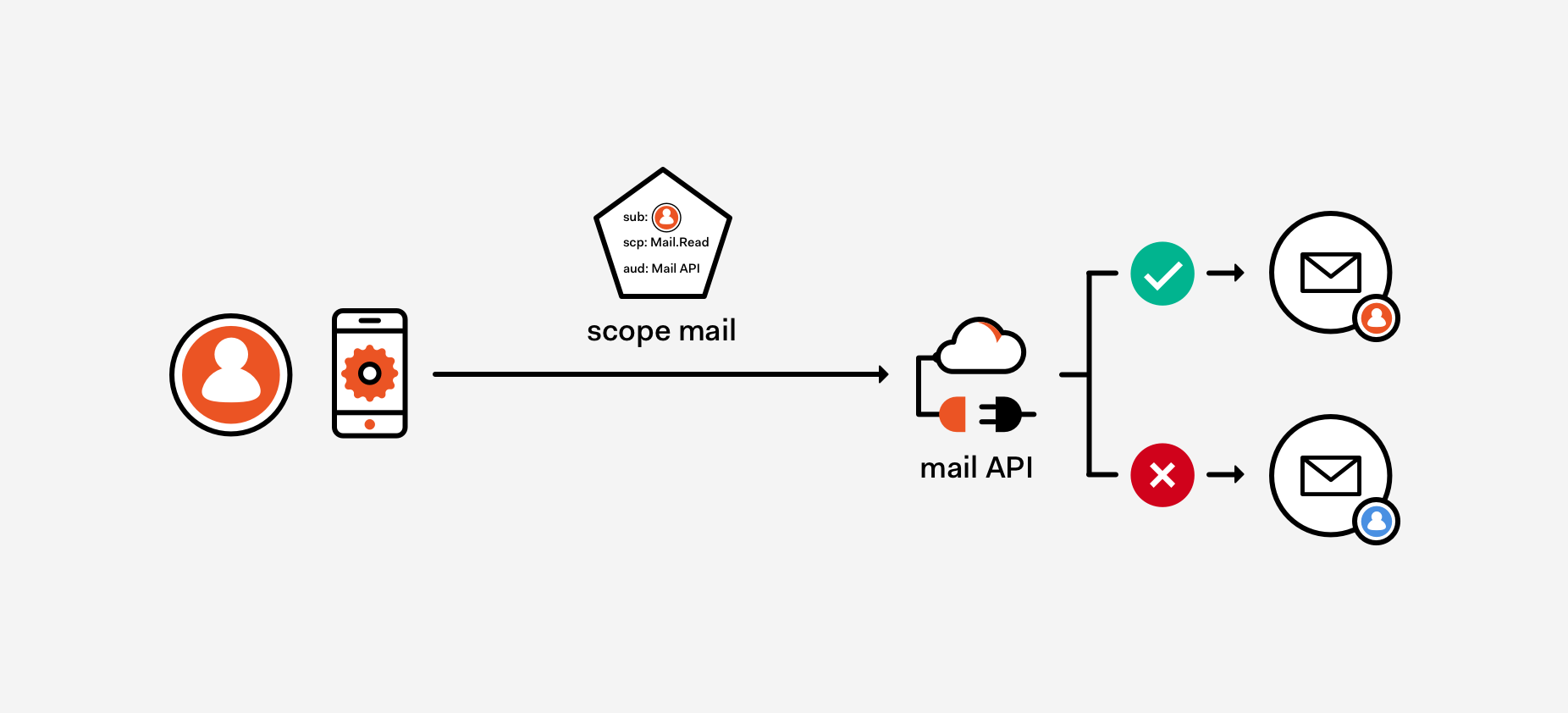
7. On The Nature of OAuth2’s Scopes
Auth0 Principal Architect and Identity expert Vittorio Bertocci on why using OAuth2 scopes in every authorization scenario is not a good idea.
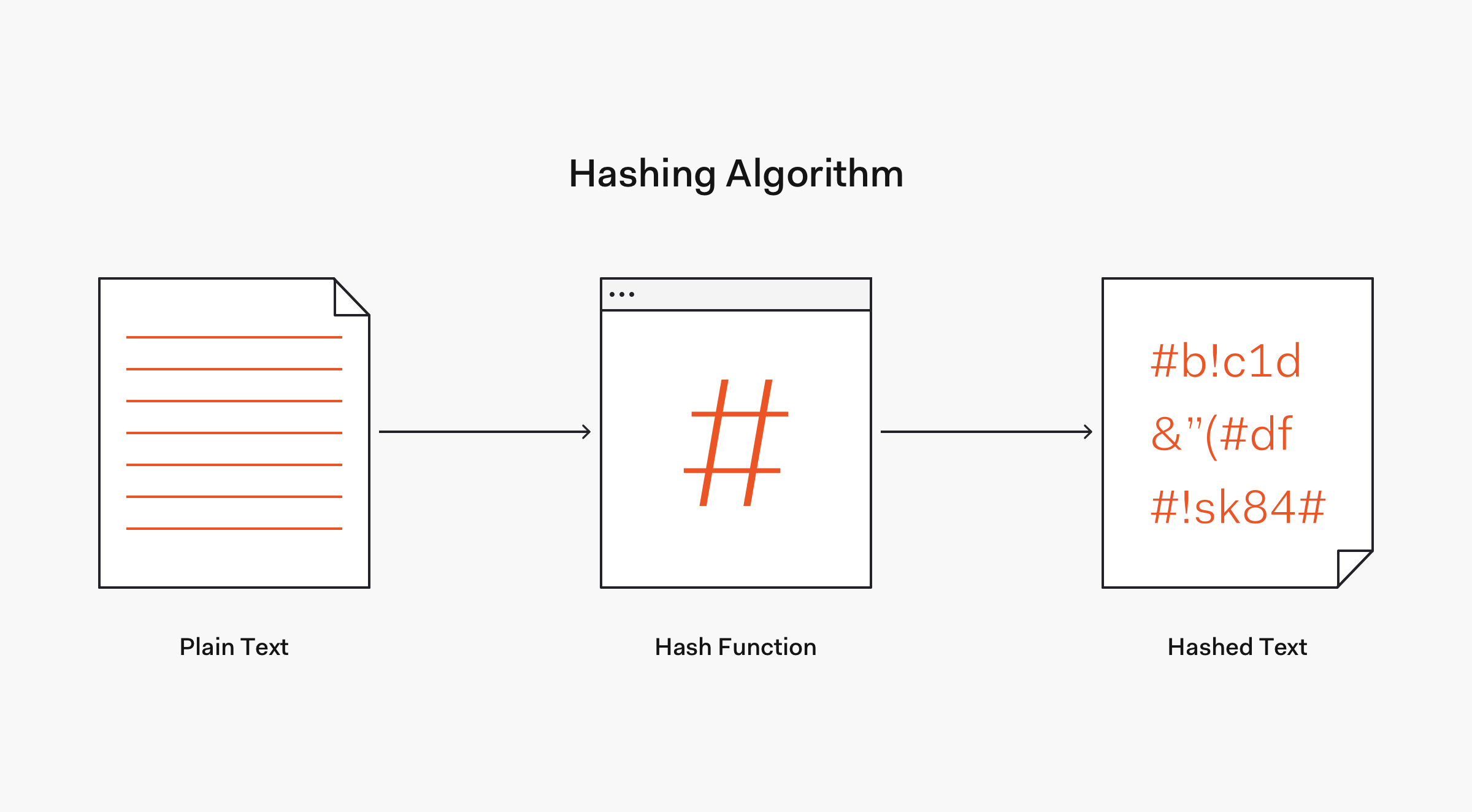
8. Hashing Passwords: One-Way Road to Security
A strong password storage strategy is critical to mitigating data breaches that put the reputation of any organization in danger. Hashing is the foundation of secure password storage.
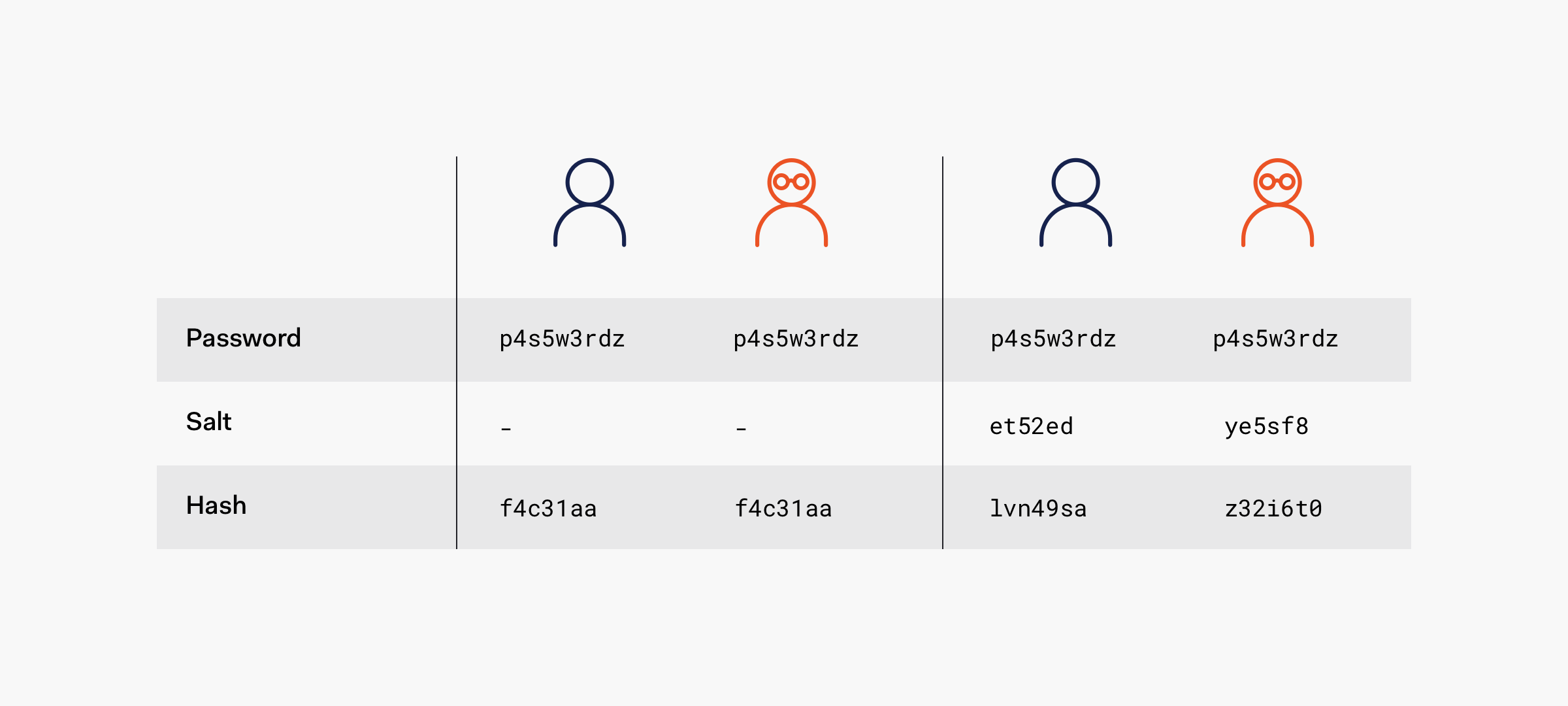
9. Adding Salt to Hashing: A Better Way to Store Passwords
A salt is added to the hashing process to force their uniqueness, increase their complexity without increasing user requirements, and to mitigate password attacks like rainbow tables
10. How Utilities Can Use CIAM to Avoid 3 Common Problems
Customer identity and management technology helps utilities reshape how they interact with users, improve their services, and tighten security.
What's Next?
We are already preparing our content pipeline for 2019. Identity and digital transformation are key areas that will keep businesses evolving to tackle challenges around privacy, usability, growth, and sociopolitical policies. We are committed to keep our content relevant to these changes and offer effective solutions through our products and services.
We'd like to take this opportunity to thank all of our readers for their consistent support and feedback. Is there anything that you'd like us to cover in 2019? Any particular identity topic or trend? Please let us know in the comments below or through social media (Twitter, LinkedIn). As always, you can subscribe to our newsletter to receive a weekly digest of our blog content.
Happy Holiday Season!
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Ramiro Nunez Dosio
Manager, Social Media