Redirect Users with Alternative Logout
You can redirect users to a specific URL after they logout. You will need to register the redirect URL in your tenant or application settings. Auth0 only redirects to allow list URLs after logout. If you need different redirects for each application, you can add the URLs to the allow list in your application settings.
Add a
returnToquery string parameter with the target URL as the value. Encode the target URL being passed in. For example, to redirect the user tohttps://www.example.comafter logout, make the following request:https://{yourDomain}/v2/logout?returnTo=https%3A%2F%2Fwww.example.com.Add the non-encoded
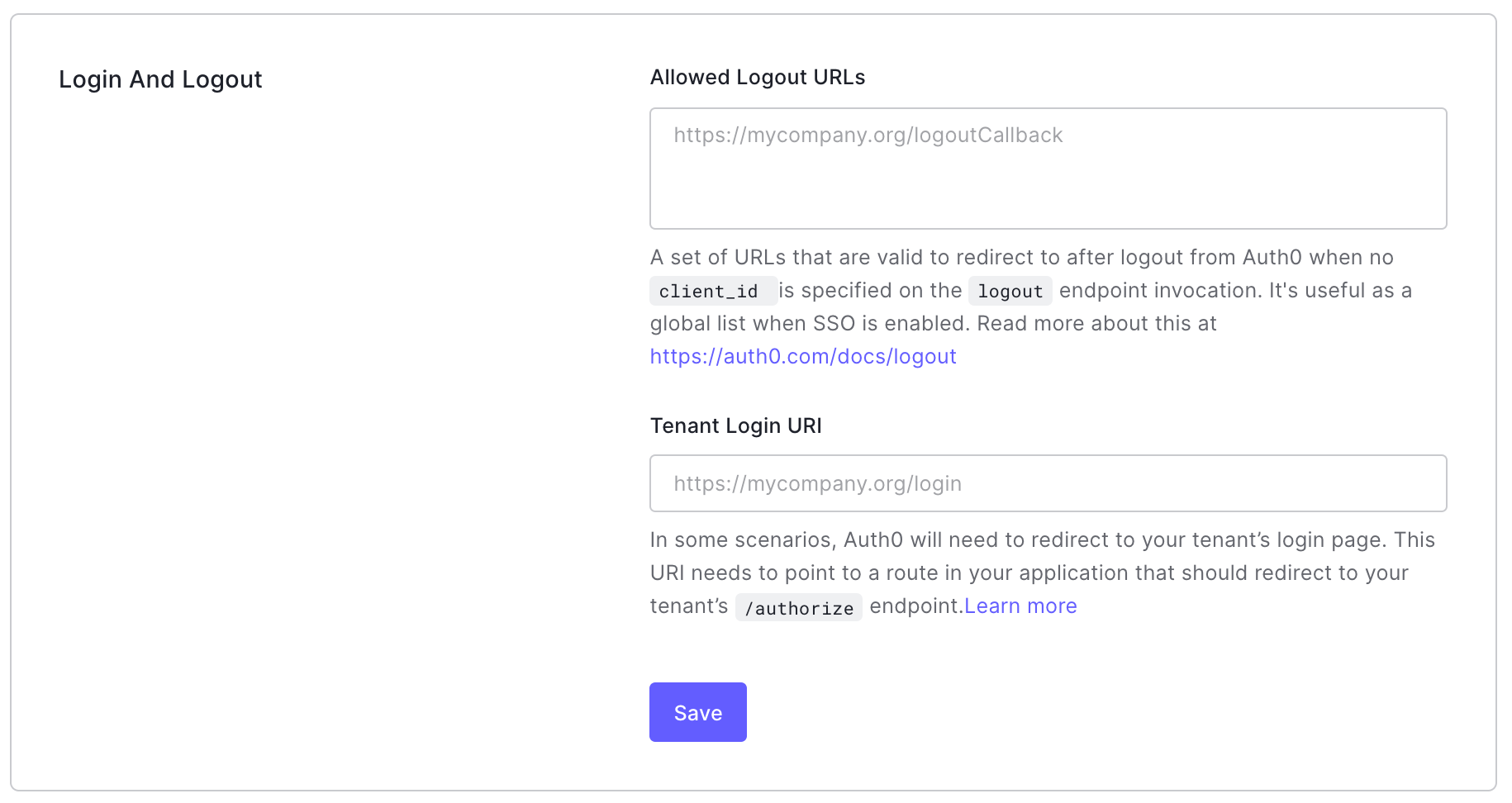
returnToURL (for example,https://www.example.com) as an Allowed Logout URLs in one of two places:Tenant Settings: For logout requests that do not include the
client_idparameter, you must add thereturnToURL to the Allowed Logout URLs list in the Advanced tab of your Tenant Settings.To add a list of URLs that the user may be redirected to after logging out at the tenant level, go to the Tenant Settings > Advanced of the Auth0 Dashboard.
Auth0 Application Settings: For logout requests that include the
client_idparameter, you must add thereturnToURL to the Allowed Logout URLs list in the Settings tab of the associated Auth0 application(s).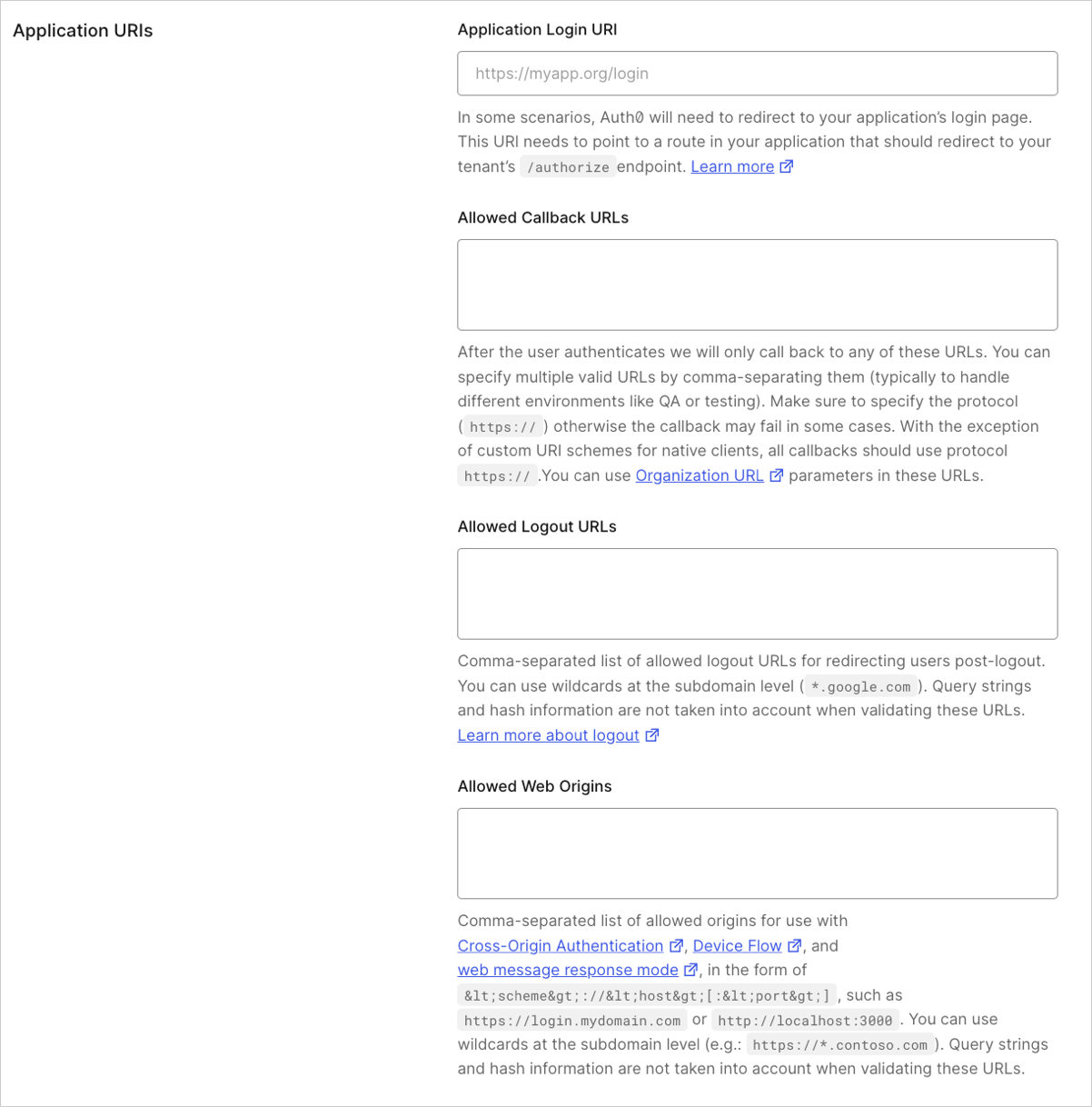
When providing the URL list, you can:
Specify multiple, valid, comma-separated URLs.
Use
*as a wildcard for subdomains (such ashttp://*.example.com).
If the client_id parameter is included and the returnTo URL is not set, the server returns the user to the first Allowed Logout URLs set in the Dashboard.
In order to avoid validation errors, make sure that you include the protocol part of the URL. For example, setting the value to *.example.com will result in a validation error, so you should use http://*.example.com instead.
Federated logouts
Several providers support federated logout.
To redirect users from applications using federated logout, initiate federated logout with the following endpoint:
https://{yourDomain}/v2/logout?federated
You are responsible for ensuring your application terminates the user session before redirecting.
When the user reaches the /logout endpoint, Auth0 terminates the Auth0 session, redirects the user to the Identity Providers logout endpoint, and terminates the session with the Identity Provider.
Limitations
The validation of URLs provided as values to the
returnToparameter, the query string, and hash information provided as part of the URL are not taken into account.The behavior of federated logouts with social providers is inconsistent. Each provider will handle the
returnToparameter differently and for some it will not work. Please check your social provider's settings to ensure that they will accept thereturnToparameter and how it will behave.The URLs provided in the Allowed Logout URLs list are case-sensitive, so the URL used for logouts must match the case of the logout URL configured on the dashboard. However, do note that the scheme and host parts are case insensitive. For example, if your URL is
http://www.Example.Com/FooHoo.html, thehttp://www.Example.Comportion is case insensitive, while theFooHoo.htmlportion is case sensitive.
If you are working with social identity providers such as Google or Facebook, you must set your Client ID and Secret for these providers in the Dashboard for the logout to function properly.
Additional requirements for Facebook
Use the returnTo parameter to specify how to redirect the user after logout.
Not all IdPs support returnTo.
For Facebook, the example code below uses the returnTo parameter and specifies a website for the redirect.
https://{yourDomain}/v2/logout?federated&
returnTo=https://{yourDomain}/logout?returnTo=http://www.example.com
&access_token={facebookAccessToken}Was this helpful?

