Auth0 is an identity platform that offers comprehensive authentication solutions to cover customers in every market sector. One of our most popular features is Single Sign-On or SSO, for short. This feature lets users sign in only once to gain access to different sites and mobile and web applications.
To help secure one of the most popular web platforms in the world with the flexibility and power of SSO, Auth0 offers WordPress developers the Login by Auth0 plugin, which provides SSO between different WordPress installs and applications on any other platform.
The concept of SSO can be a little confusing for developers and site administrators that may be new to it. So in this post, we'll explore the different concepts associated with SSO and how our WordPress plugin can help you.
What Is SSO?
SSO allows multiple apps to share a single session from a central provider. Users log in once, in this case to an authorization server powered by Auth0, to establish the main session and then are redirected to the application to establish a session there. When that user visits a different site or application associated with the same authorization server, the existing first session is used to create a session without having to log in again.
When you delegate authentication, you hand off the responsibility of verifying a user's credentials (such as username and password) to a third party. In this post, that third party is Auth0 but it could also be Google, Facebook, or another identity provider. For SSO to work, you need to have two sessions:
- The session with the Auth0 authorization server, created when you log in.
- The session with WordPress, created when you're redirected back after logging in.
At Auth0, we use the term tenant to indicate a particular namespace. When you sign up for Auth0, you choose a tenant name which becomes part of your Auth0 domain used for OAuth and API endpoints.
When you log in to the Auth0 dashboard, the controls and menus that you see are for the specific tenant you are using. If you create a second tenant or are added to an existing one, you can switch tenants from the menu on the top right. The name next to your avatar is the tenant that you are currently using.
This tenant is a logical boundary around Auth0 functionality like Applications, Connections, Users, Rules, and more. All the Applications within a tenant can share a session (in other words, can use SSO between them) and can use the same Connections to log in if configured to do so.
This means that once you login to Auth0 and establish the first session, all the applications for that same tenant can use that session to determine whether the user is logged in or not. For the user, the process looks like this:
- Click "Login" on App 1
- Log in with Auth0
- The user is now logged in with App 1
- Visit App 2 and click on "Login" there. Note: The user may also be redirected to log in from a page that requires authentication
- The user bypasses any login forms and is now logged in with App 2 as well
- Visit App 3 and click "Login"
- The user is then logged in with App 3 as well
For a more detailed description of how this process works, see our Single Sign-On with Auth0 document.
As you can see, this is a great way to create a simple, low-friction authentication experience for users in your network of sites and apps. Learn more about SSO, here.
How Does Single Sign-On (SSO) Work in WordPress?
SSO in WordPress works the same as above, just replace "App" with "WP Site" anywhere in the process. SSO can happen between WordPress sites as well as with other web or mobile applications. As long as the different instances are using Auth0 and a browser for authentication, you can use SSO between them.
Let's see how that works in a little more detail:
- Users request a restricted page or try to take an action that requires authentication (like accessing the profile page).
- The site checks for a session in WordPress with
is_user_logged_in()(this checks for a specific cookie set by WordPress on login). - If there is no session, users are redirected to check for an Auth0 session.
- If users already have a valid session with Auth0 (they are already logged in to Auth0 and it has not expired), they are prompted (if desired) to continue with the same account then redirected back to WordPress.
- Once redirected, the Auth0 authentication is verified and the WordPress session is re-started.
- Users proceed to view the restricted page or carry out the action they wanted to take.
While there is a lot going on behind the scenes, most of this will be transparent to the users. Their session was renewed without asking for credentials again and they were able to continue with their action.
This process works whether the users have an account with the second (or third or fourth) WordPress site or not. The plugin can be configured to allow new accounts to be created from Auth0 users even if site registration is turned off. This allows new sites to be added without requiring known users to register!
Additional Benefits of Enabling SSO
The benefits of enabling SSO for a network of sites and applications aren't limited to just simplifying the user experience, but also include storing users in a central location and improving sign-up conversions. You can easily bring these benefits to your WordPress project by implementing SSO with Auth0.
Auth0 connects to many different identity providers while also providing you with a central user database that can be associated with some or all of your WordPress sites and applications. This central user database creates a single source of truth for all user data and allows you to efficiently search for and update users in the dashboard or using our Management API.
A single database for multiple sites also allows you to streamline and enforce security measures across all the sites that use it. Password strength and composition, as well as username restrictions, can be enabled and managed in one place, improving the security of all sites within the network.
Finally, Auth0 provides additional login security, particularly when using the Universal Login Page. The WordPress login page URL is standard across all sites, making it a common target for enumeration and DDoS attacks. Putting Auth0 in front of your authentication flow protects from as-yet-unknown vulnerabilities, out-of-date core code, and additional holes that might be opened by plugins.
"Discover the benefits of enabling SSO in your WordPress applications."
Tweet This
Does SSO Work with Multisite Networks?
The Login by Auth0 plugin is regularly tested with WordPress multisite. That means that multisite networks can use SSO between networks with the same benefits as single sites. Network administration (such as managing access to each site for each user) still happens in WordPress but the initial authentication will happen in Auth0. To be clear, SSO with Auth0 does not happen between sites within a WordPress multisite network but can between networks.
There are some considerations regarding setup that are covered in our Auth0 WordPress plugin installation documentation. Also, the plugin settings can be set via PHP constants and will map to all sites in the multisite network. If you have any questions about plugin configuration or how it works, please see the end of this post for a link to our Community channel where you can connect with other WordPress developers like you using Auth0.
Try WordPress SSO with Auth0 Out
The best way to see how WordPress SSO works with Auth0 is to try it out yourself. This will require setting up two different WordPress sites and connecting them through Auth0. You can set this up between two existing sites but please note that while the Auth0 plugin is not destructive (it will not delete users, metadata, or roles), it does take control over your login process so it’s best to try the setup on test/development sites or on sites that only use authentication for site administration. Deactivating the plugin will return the login process to its original state.
For this setup and testing process, make sure to use the same browser window (separate tabs are fine) to guarantee that you’re using the same cookie store to make SSO work.
First, sign up for an Auth0 account here (it’s free for up to 7,000 users). If you want to get more familiar with the dashboard and what Auth0 has to offer, follow the tutorials that appear. Don’t worry about creating Applications or Connections for your test WordPress sites, that’s all done automatically during plugin setup.
Next, decide which two sites you want to connect, log in as an administrator and install the Login by Auth0 plugin on both (the login page will not change until the plugin is configured).
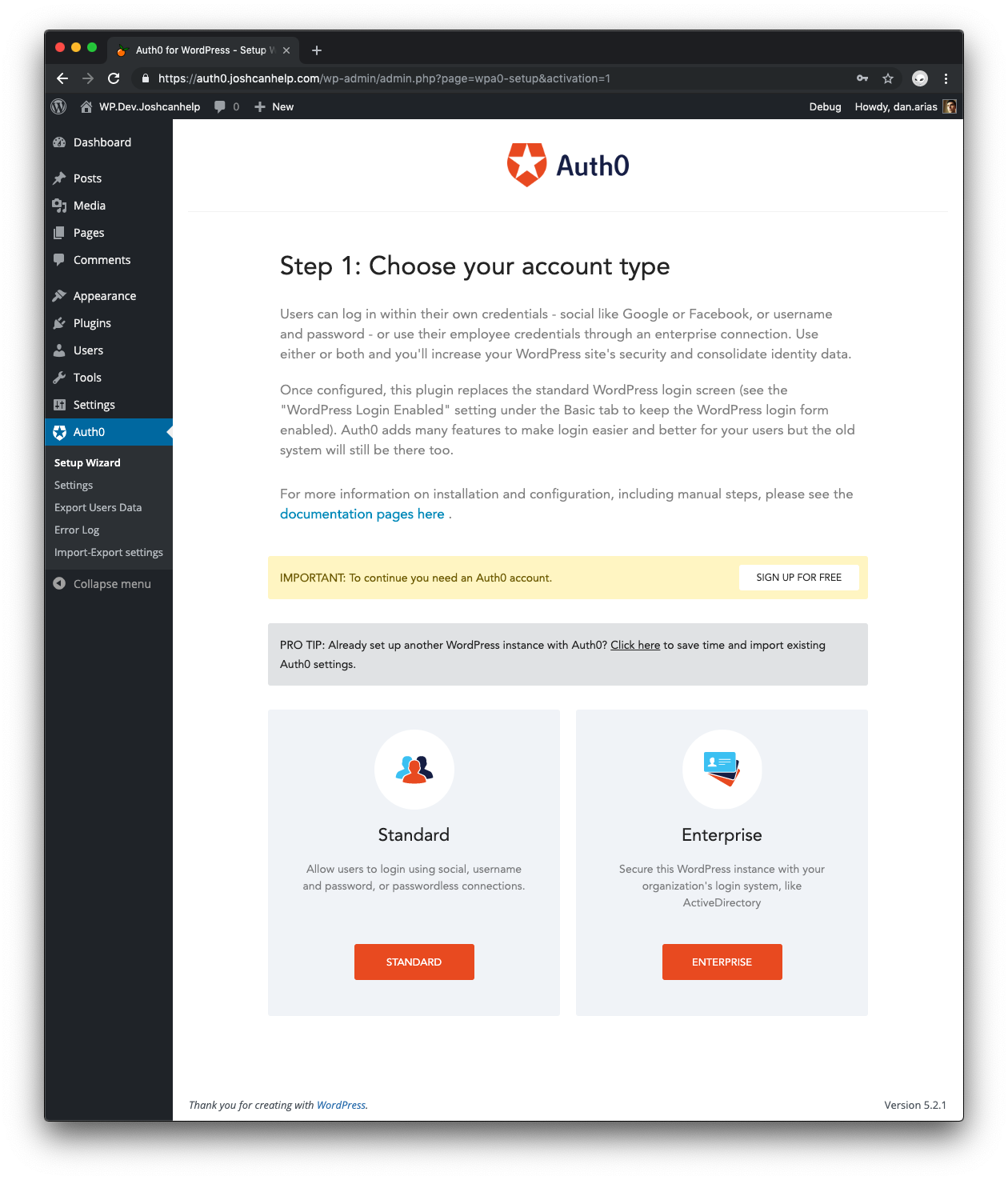
On one of the sites, activate the plugin and you’ll be redirected to a Setup Wizard.
Follow the Standard Setup instructions from this document to create an Application, Database Connection, and a user account for yourself. Before continuing, check your email and click on the verify email link that was sent.
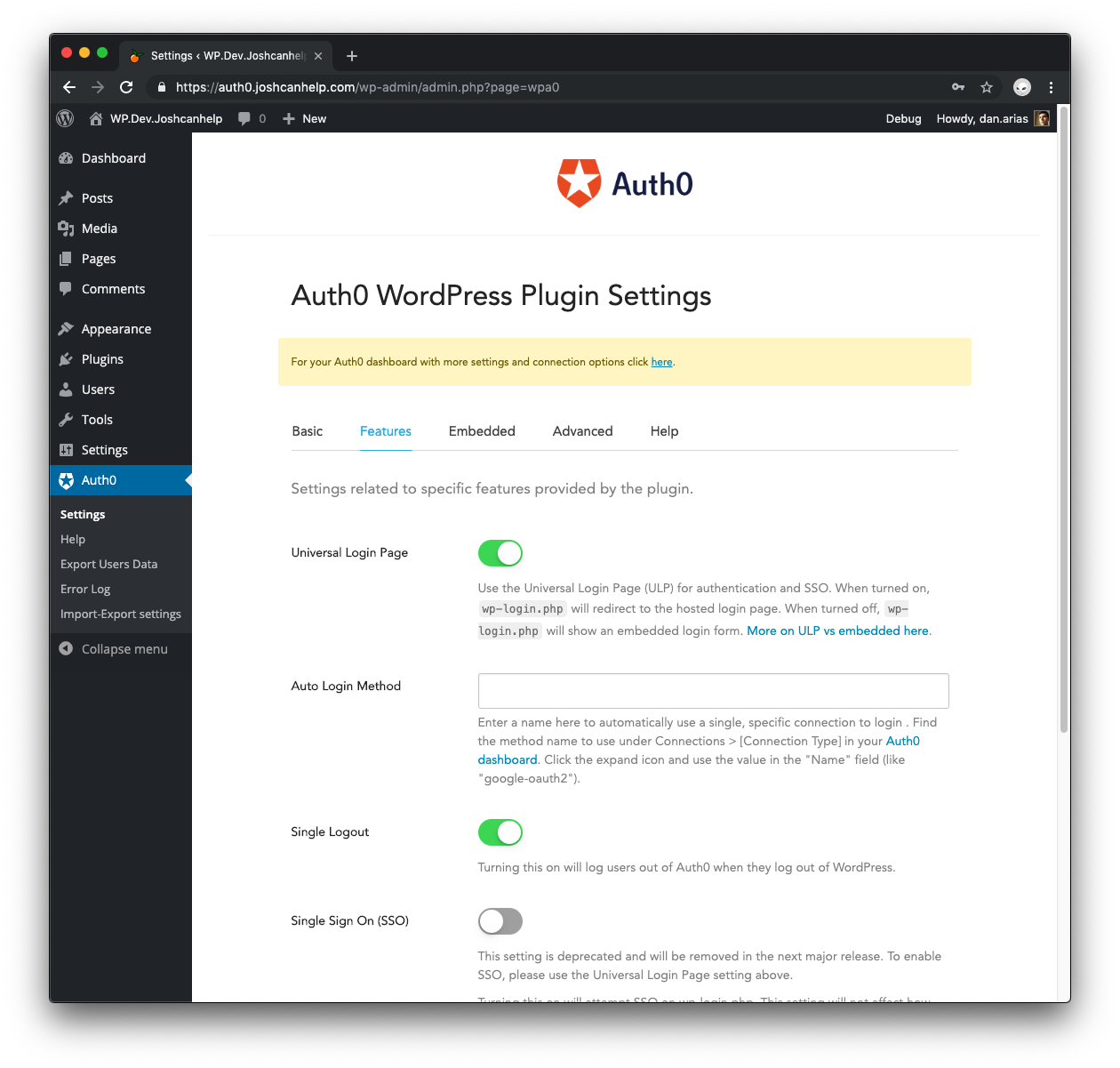
Once the setup is complete, go to Auth0 > Settings > Features tab in your WordPress admin and make sure that Universal Login Page is turned on (this is a default setting in the latest version of the plugin).
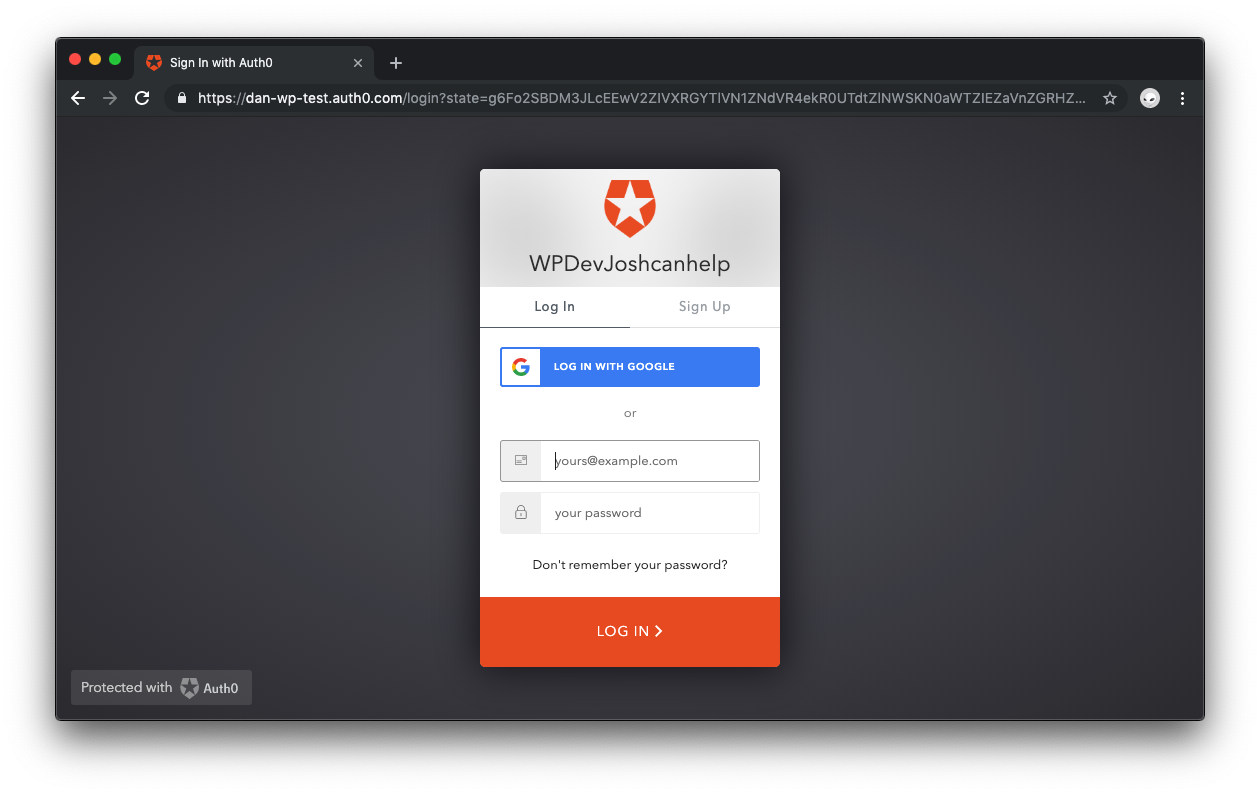
To test that everything is working properly, log out of WordPress, then visit the wp-login.php page. You should be redirected to the Universal Login Page on Auth0.
Try logging in with the same credentials used during Auth0 WordPress plugin setup to make sure it’s working properly.
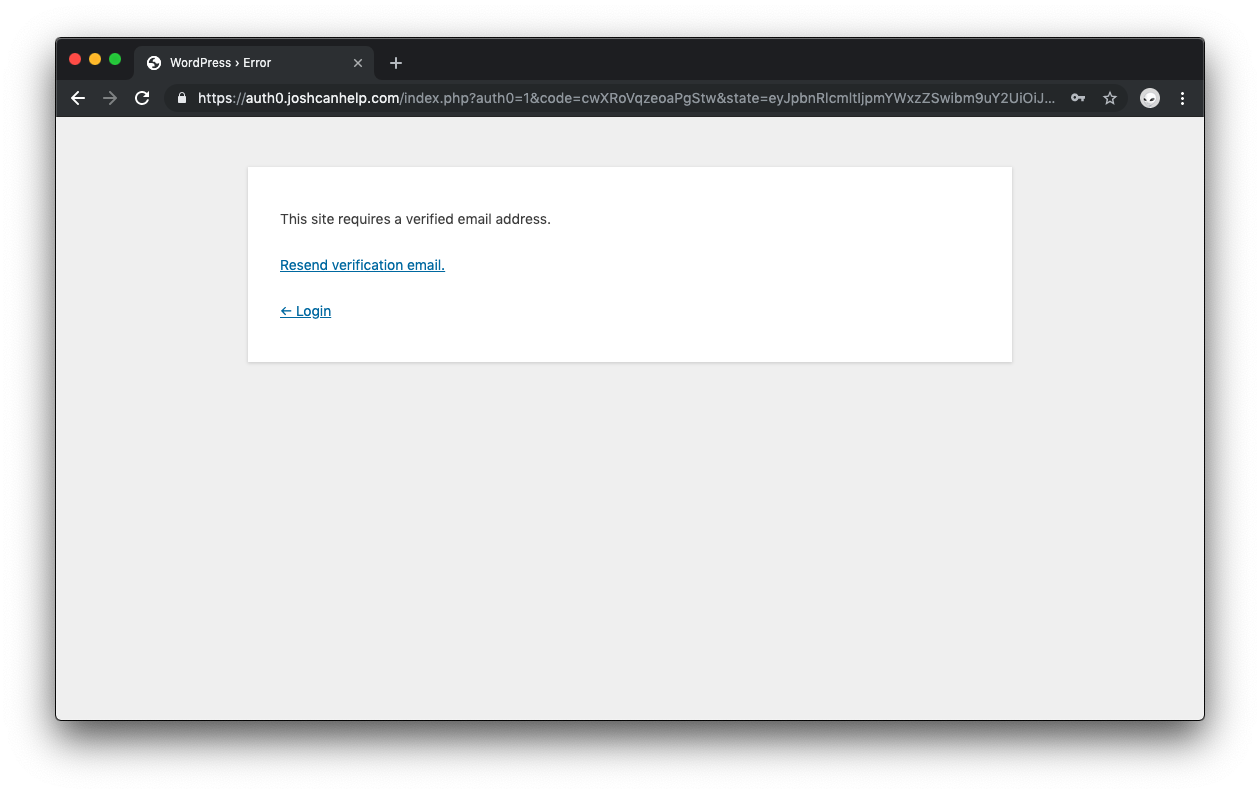
If your site is set up to require verified email addresses, you'll see the following page if you haven't done so:
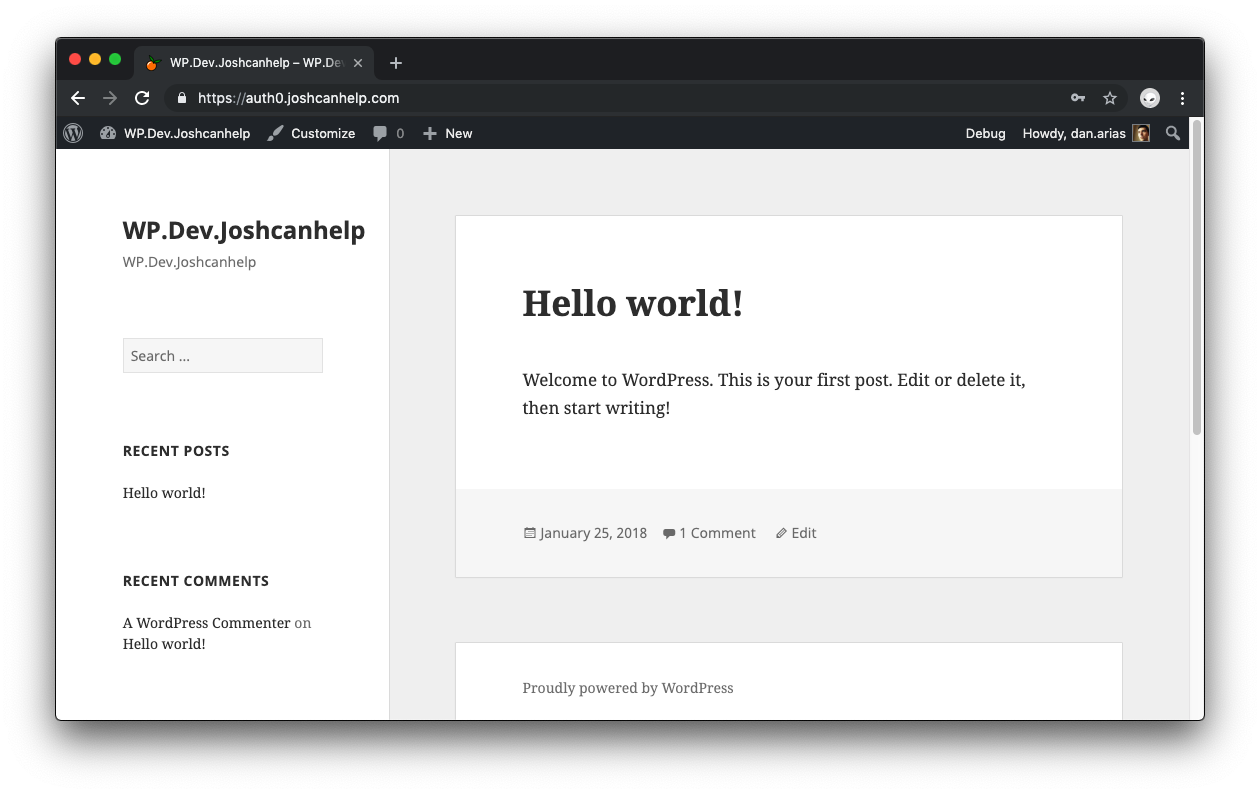
Once you are logged in, you'll see the home page of your first site:
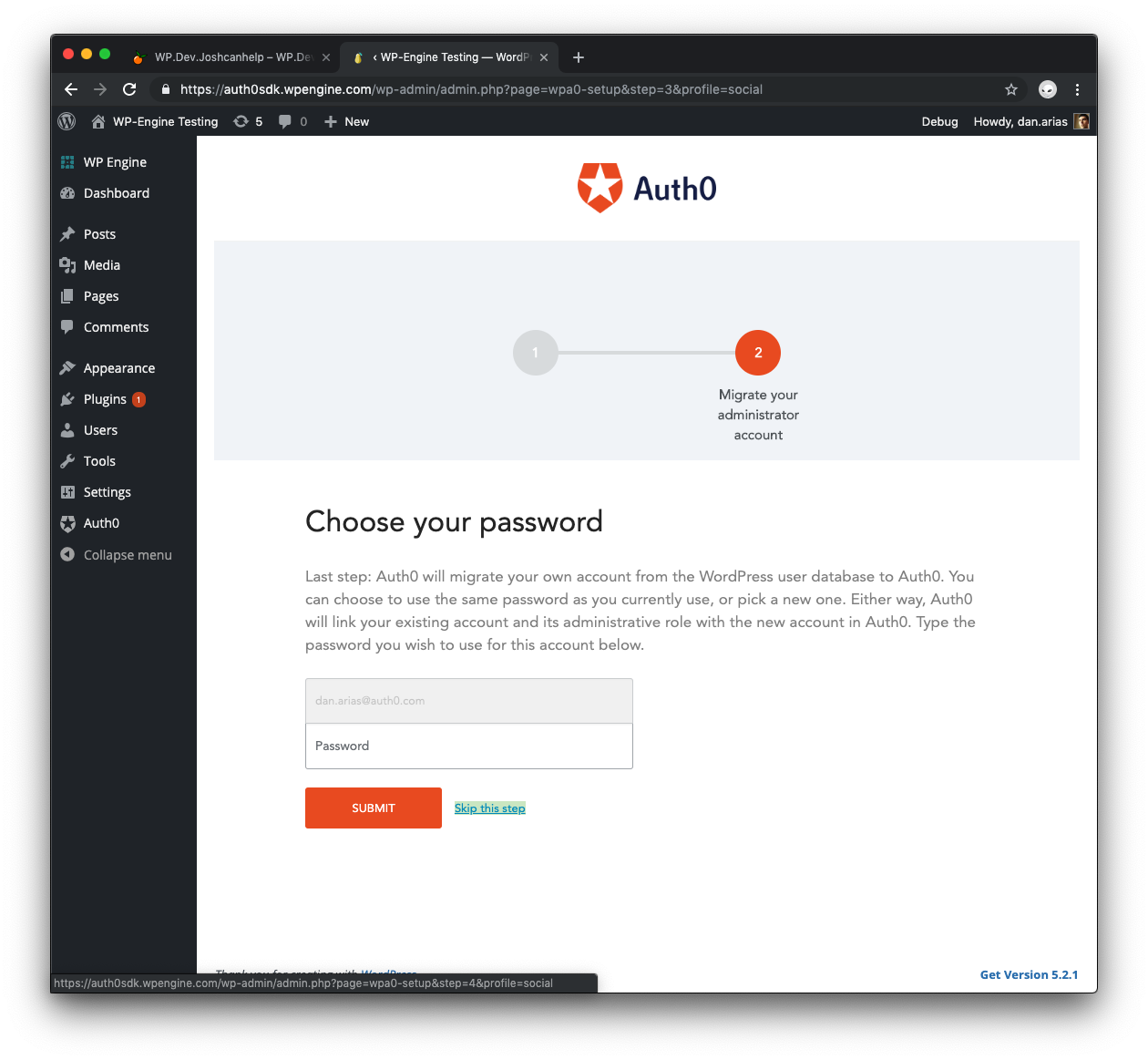
On the second site, follow the same procedure to install and activate the plugin. There's one difference to have in mind when running through the Setup Wizard: on the screen where you’re asked for an admin password, click Skip this step.
You're going to use SSO to link your Auth0 account to your WordPress one. Once the setup completes, go to Auth0 > Settings > Features tab in your WordPress admin, make sure that Universal Login Page is turned on, and turn Single Logout off.
The Single Logout feature logs users out of Auth0 when they log out of WordPress. By turning this off, you allow users to keep an active session with the Auth0 authorization server even after they log out from one of your sites. Users are also allowed to log back into one of your sites using SSO and without having to re-enter their credentials.
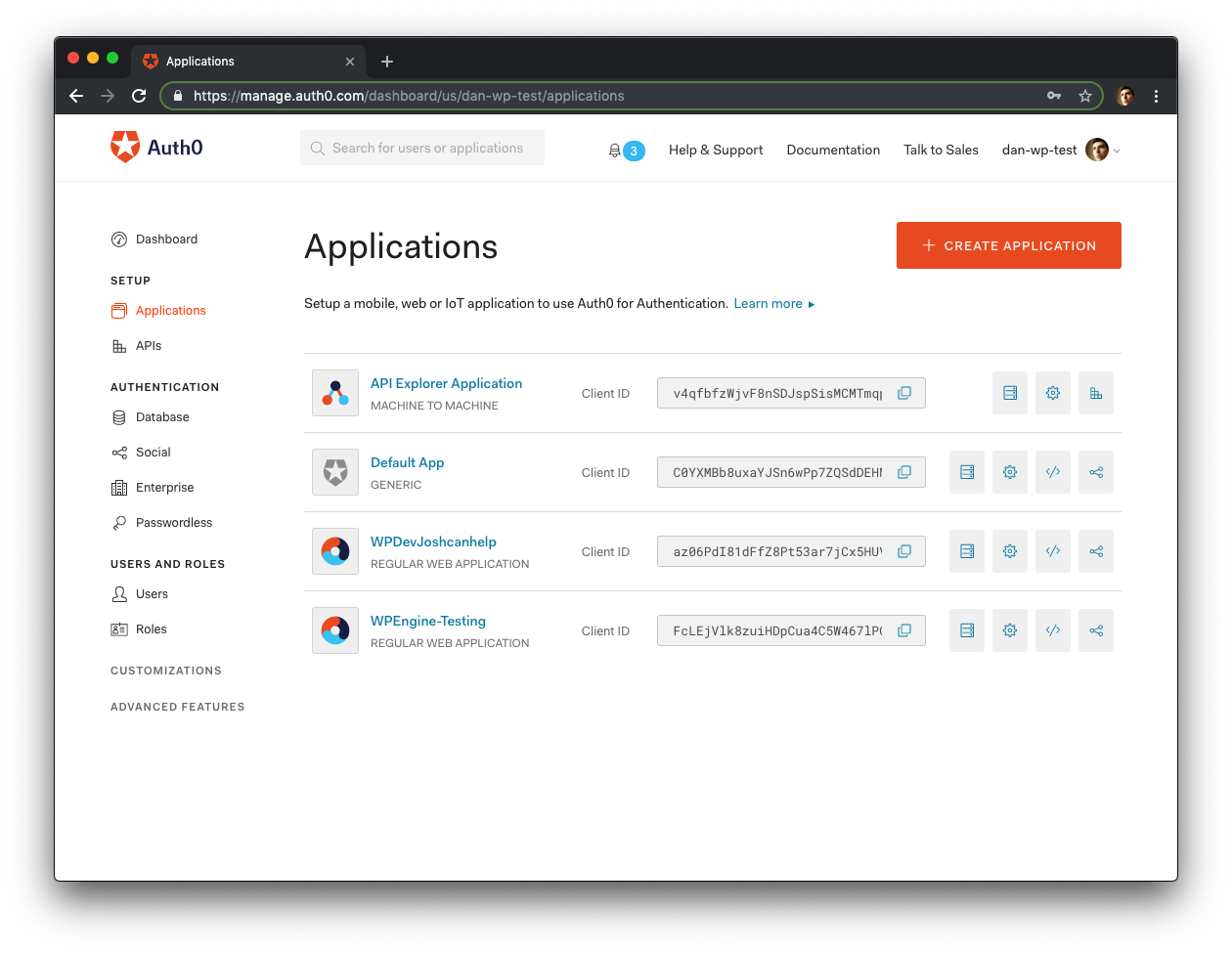
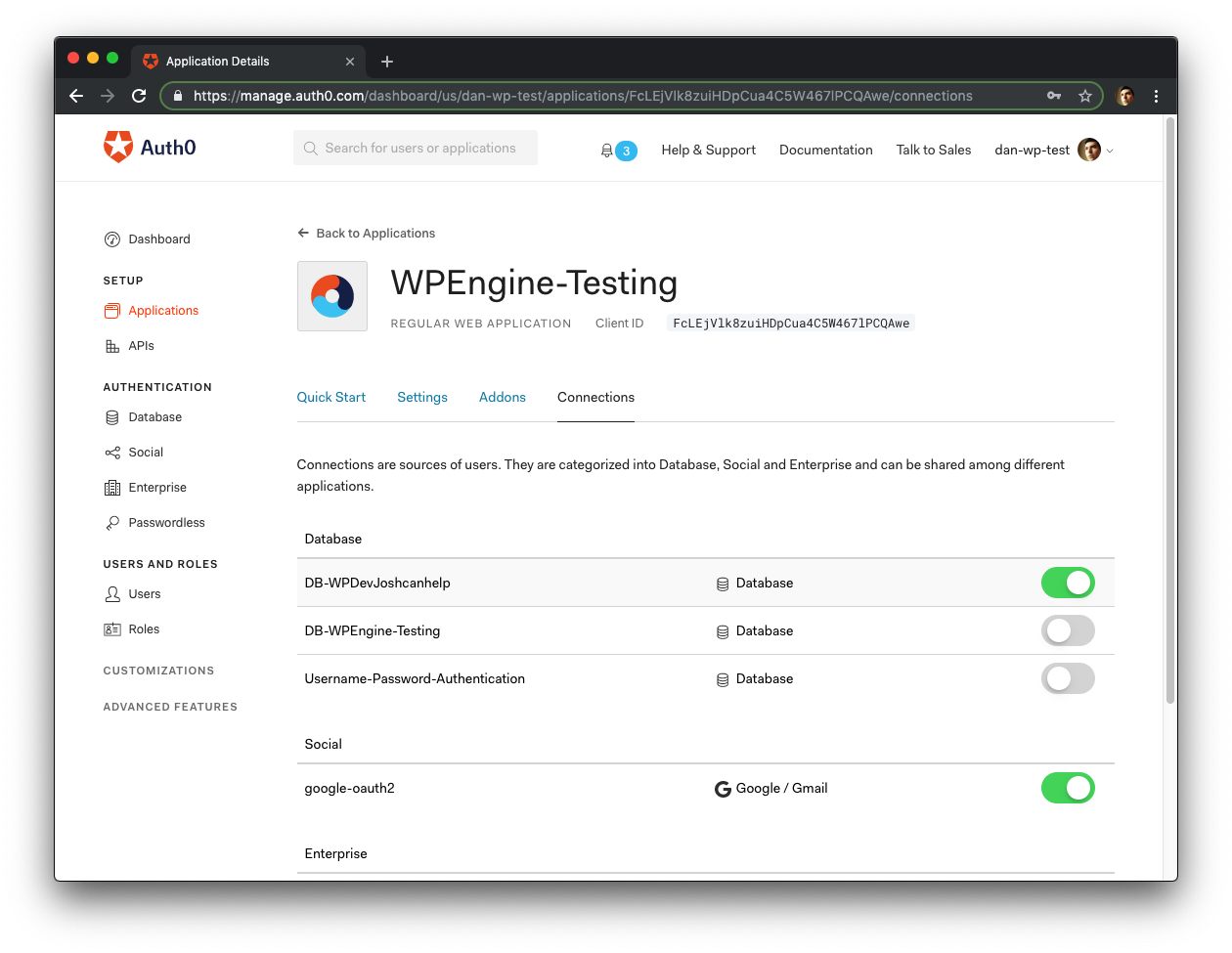
Next, go to your Auth0 Dashboard > Setup > Applications and select the Application created for the second WordPress site.
If your dashboard looks different than the screenshots above, go to Auth0 Dashboard > Applications to select the application.
Click the Connections tab, turn off the database Connection created for this site, and turn on the Database Connection being used for the first site.
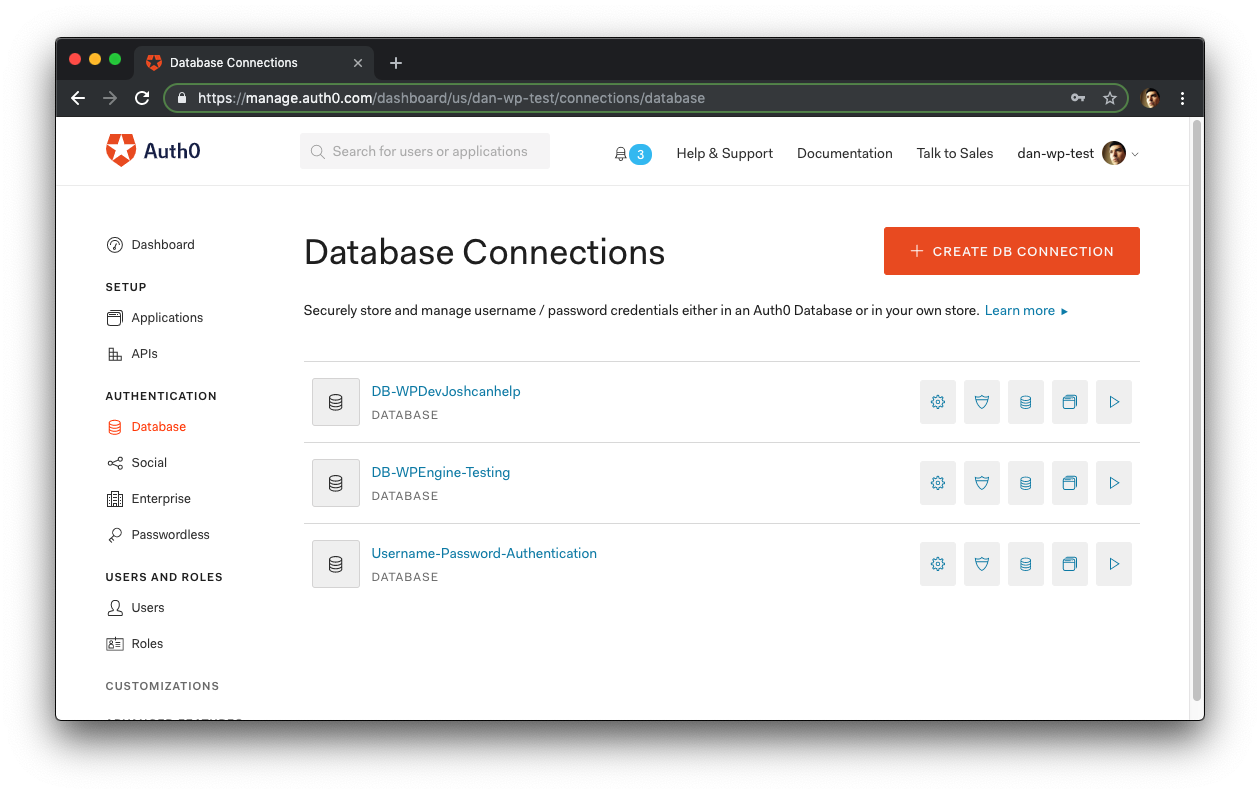
To avoid confusion, go to Auth0 Dashboard > Authentication > Database and delete the Connection created for the second site.
If your dashboard looks different than the screenshots above, go to Auth0 Dashboard > Connections > Database to delete the second database.
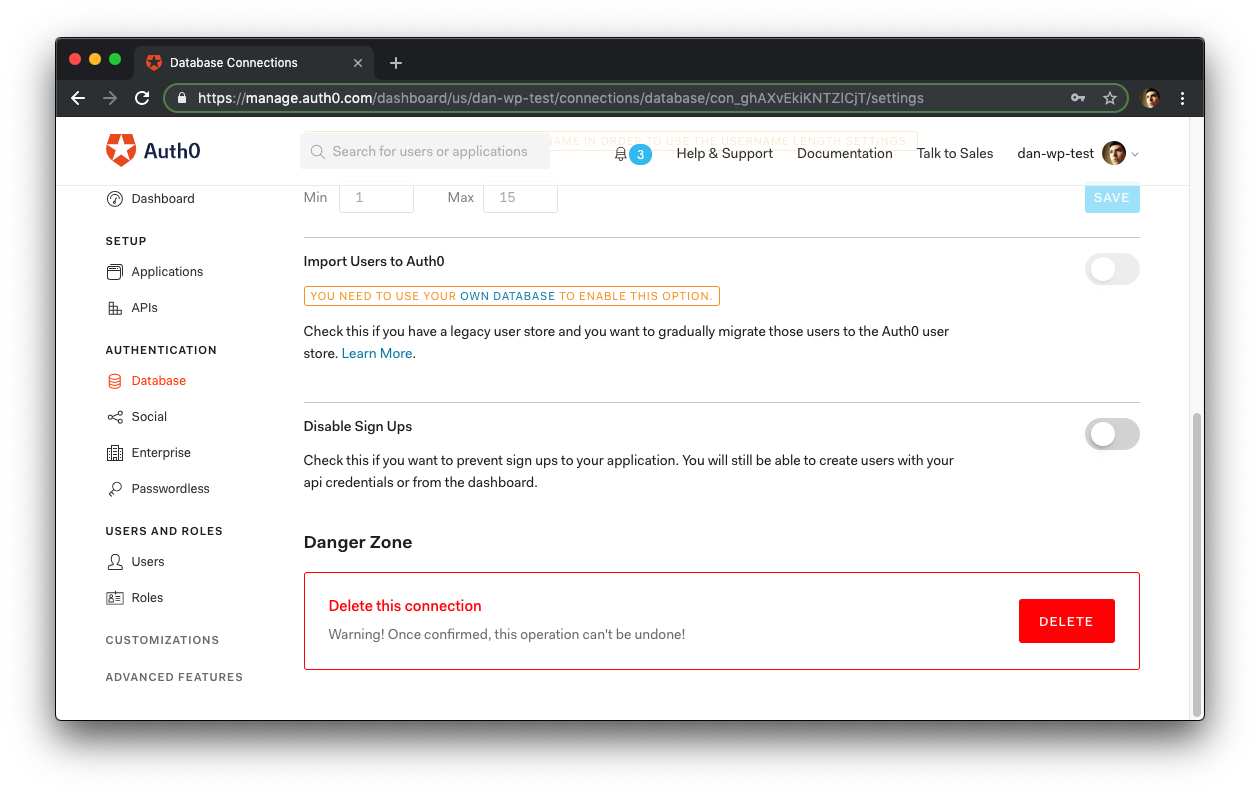
Select the database of the second WordPress application from the list and scroll down until you see a red button named "Delete" and click it:
Finally, confirm the database deletion in the modal that comes up.
You now have two Applications and one Database Connection that’s activated for both.
On the second site, you want to test that the account that was created during the setup of the first site, the one tied to the session created at Auth0, maps to the second site. Log out of the second site and visit the wp-login.php page. You will see a pause in your browser followed by the homepage of your second site, where you are logged in.
Congrats, you just set up SSO between two WordPress sites! You can follow the steps for the second site for as many WordPress sites as you need. Just make sure they are all using the same Database Connection so that same Auth0 user account is used across applications.
"Learn how simple and easy is to add SSO to WordPress apps using Auth0."
Tweet This
Summary
We hope you learned a bit about SSO in general and, specifically, how it works with WordPress. If you have any questions about capability, configuration, or anything else, please post in the thread below and we’ll be happy to help!