sample
Okta, Inc. (NASDAQ:Okta) announced on 3/3/2021 that it has entered into a definitive agreement to acquire Auth0 in a stock transaction valued at approximately $6.5 billion. Together, Okta and Auth0 address a broad set of identity use cases, and the acquisition will accelerate the companies’ shared vision of enabling everyone to safely use any technology, shaping the future of identity on the internet.
Auth0 will operate as an independent unit inside of Okta, and both platforms will be supported and invested in. As a result, organizations will have a wider breadth of identity solutions to fit their unique needs. Okta and Auth0’s comprehensive, complementary identity platforms are robust enough to serve the world’s largest organizations and flexible enough to address every identity use case, regardless of the audience or user.
Sign In
In the demo client, click on the Sign In button. The client will redirect you to the Auth0 Universal Login page to log in or sign up. Since this may be the first user you are adding to Auth0, go ahead and click on the Sign Up link at the bottom of the form. Then, provide an email and password to register a new user.
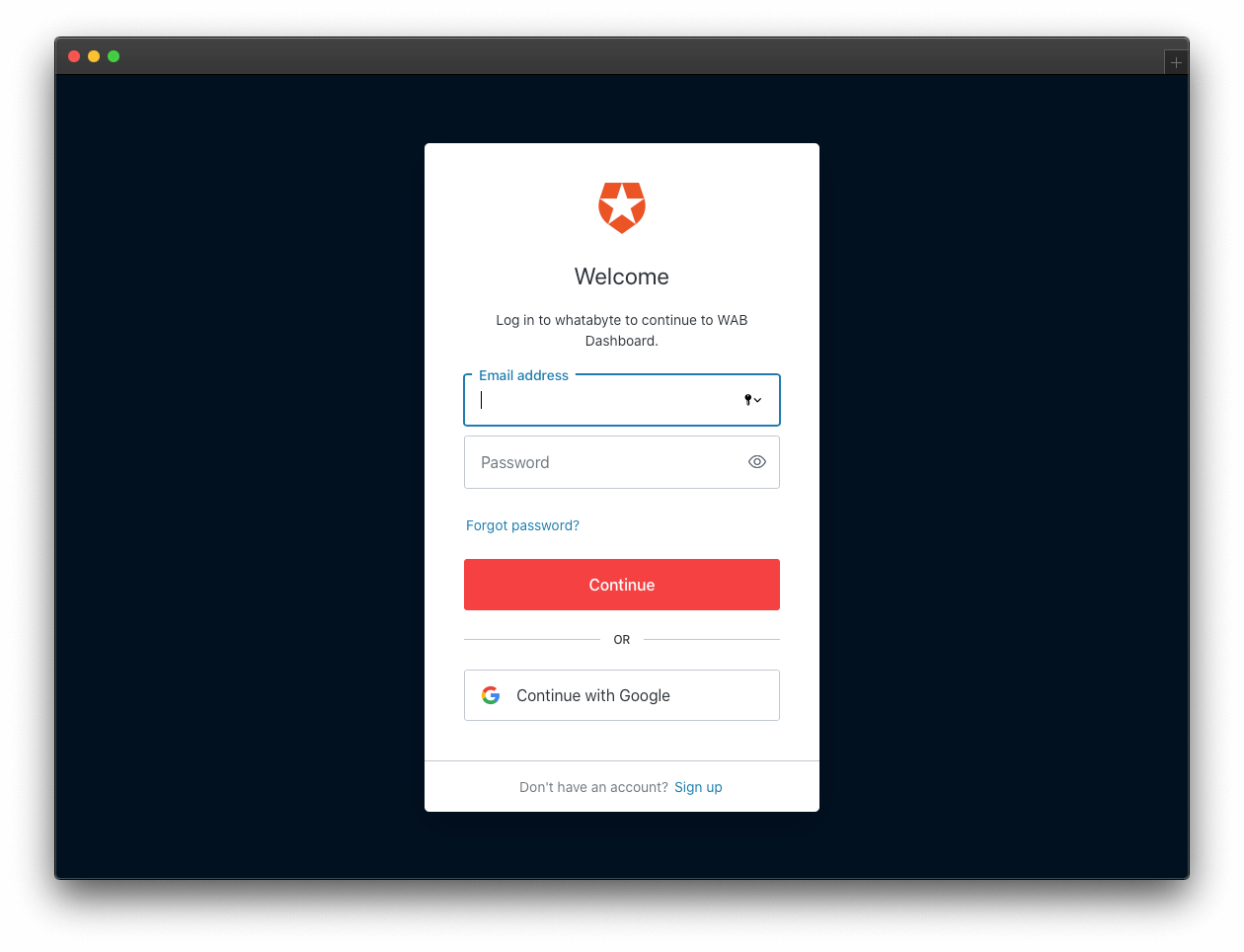
Once you sign in, the user interface of the demo client changes:
The Sign In button becomes a Sign Out button.
You can find a user tab below the Sign Out button.
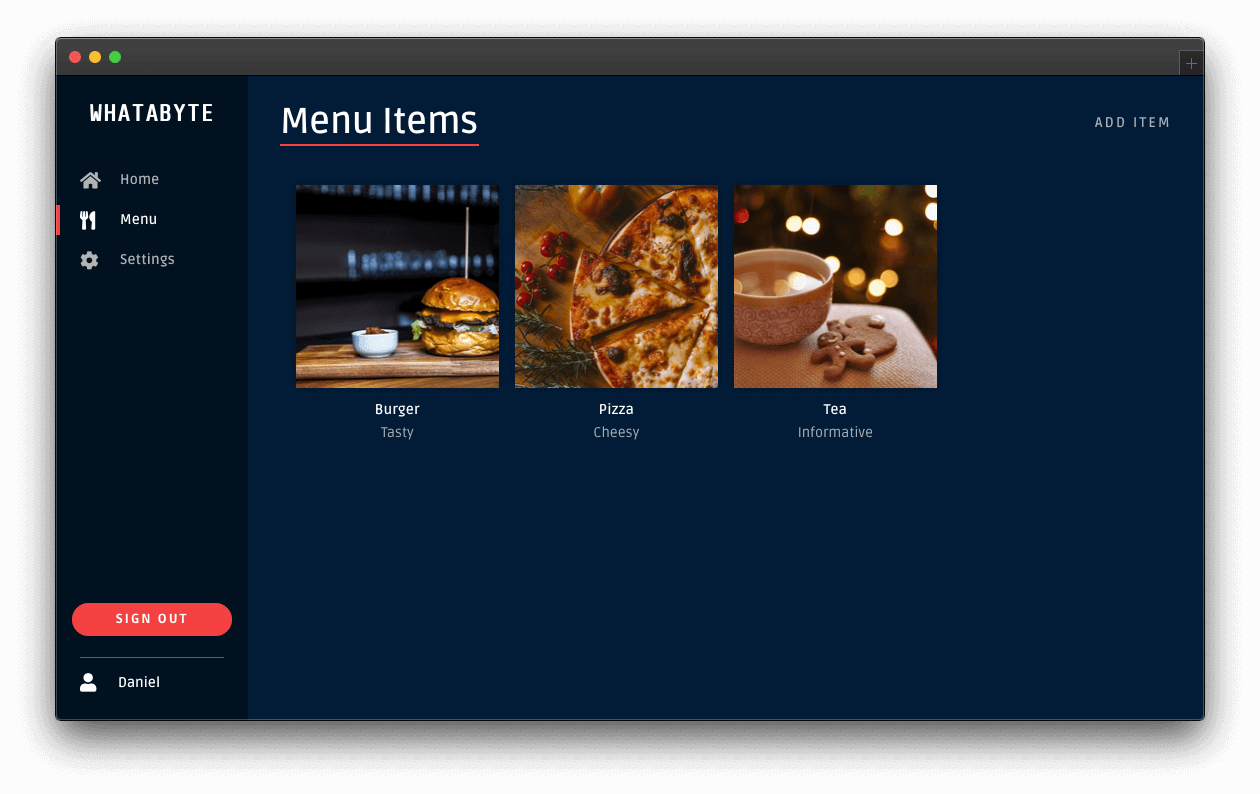
Click on the user tab to see a profile page with your name or email as the title and your profile picture — if you signed in with Google:
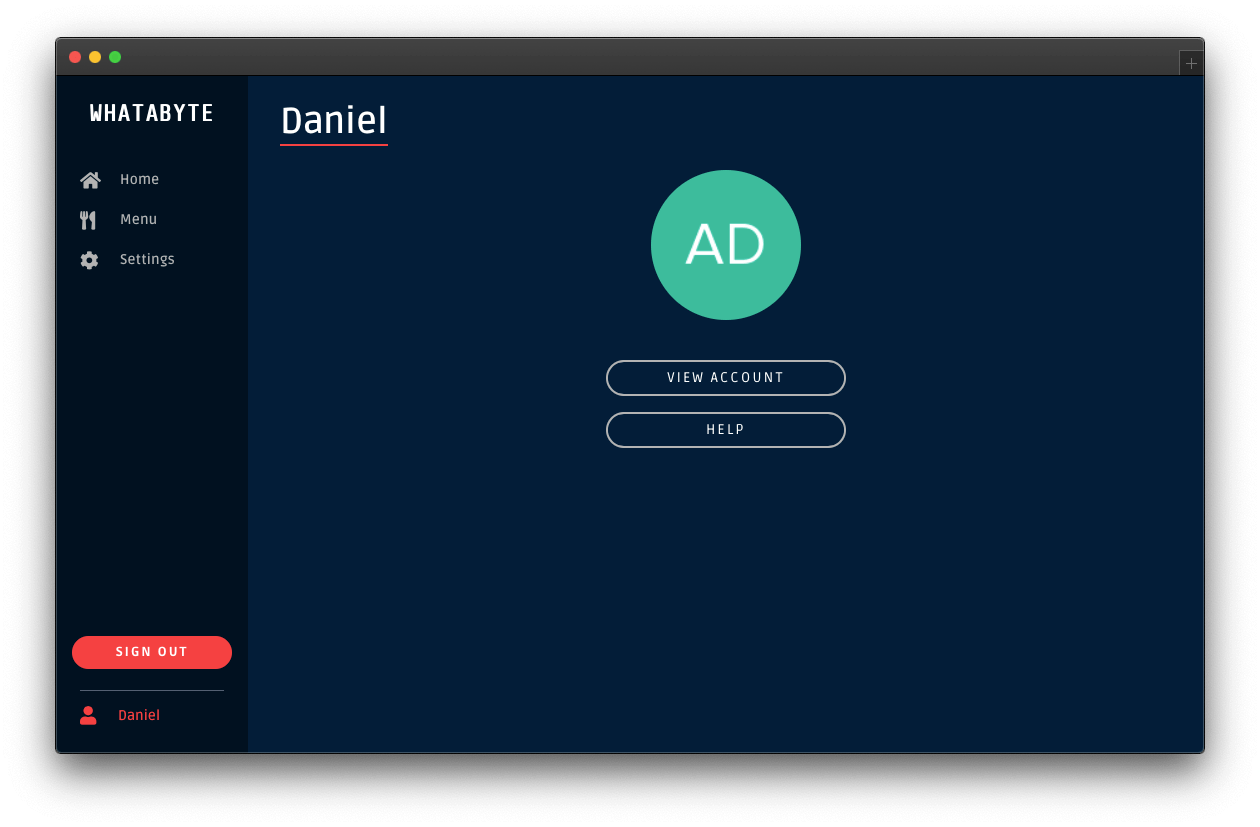
The demo client caters to three types of users:
Unauthenticated visitors: any visitor who has not logged in — some literature may refer to this type of user as "guest" or "anonymous".
Authenticated users: any visitor who successfully logs in.
Admin users: any authenticated user with the
menu-adminrole.
The end-goal of this tutorial is to use the menu-admin role and its associated permissions as access control artifacts. The plan is to only allow admin users to create, update, and delete menu items in the WHATABYTE Dashboard. In the Role-Based Access Control (RBAC) section of this tutorial, you'll create the menu-admin role, associate permissions with it, and assign it to a new user that you'll create through the Auth0 Dashboard.
However, you'll start with protecting your API write endpoints against unauthenticated visitors.
Experiment with the demo client:
Add items by clicking on the Add Item button located at the top-right corner of the "Menu" page.
Click on items and try to edit them or delete them.
You can do any read or write operations right now.
Security Exercise: Test your endpoint protection
Log out from the demo application.
Click on the Settings tab on the left-hand navigation bar of the demo client. Then, click on the Modify button.
The "Auth0 Demo Settings" page loads up. Disable the authentication features:
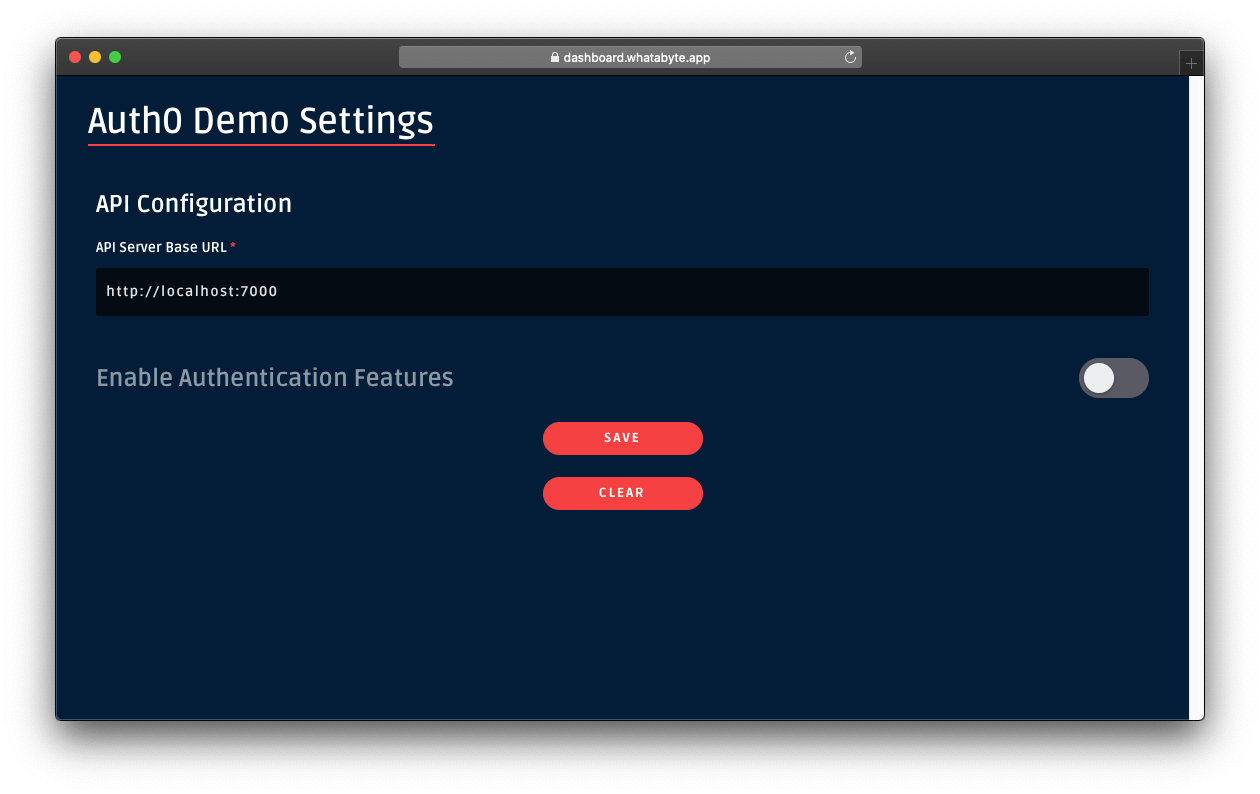
Click on the Save button.
Once the demo application loads again, click on the Menu tab. You'll notice that the Add Item button is now visible. In this mode, the demo client lets you access UI elements that make requests to your API write endpoints as an unauthenticated visitor. As such, those requests won't include an access token. If your API security is working correctly, it should reject those requests.
Click on the Add Item button to open a pre-populated form and click on the Save button. You'll get an error, No authorization token was found:
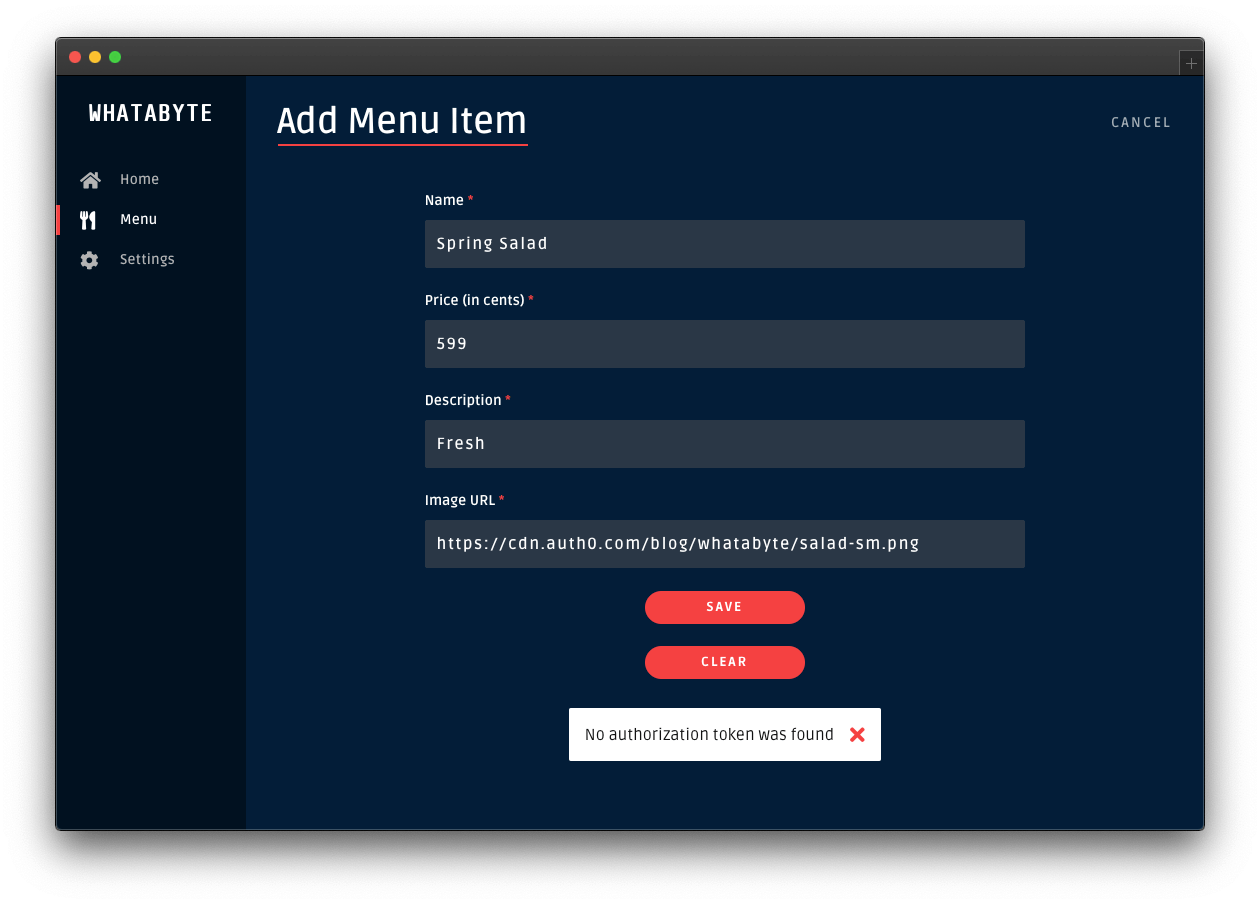
Click on the Cancel button in the "Add Menu Item" page. The "Menu Items" loads again. Click on the "Burger" item and try to edit it or delete it.
Those two actions will also fail:
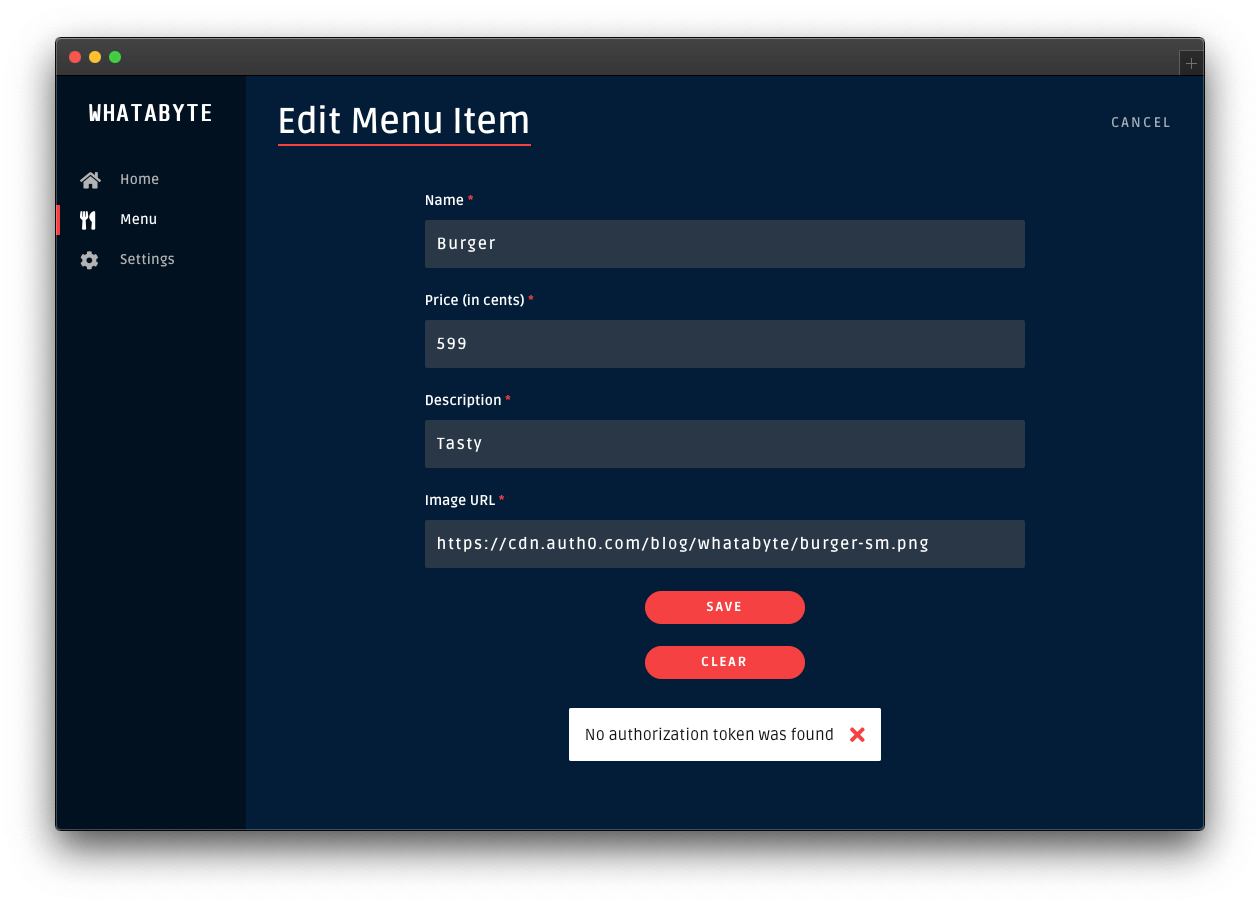
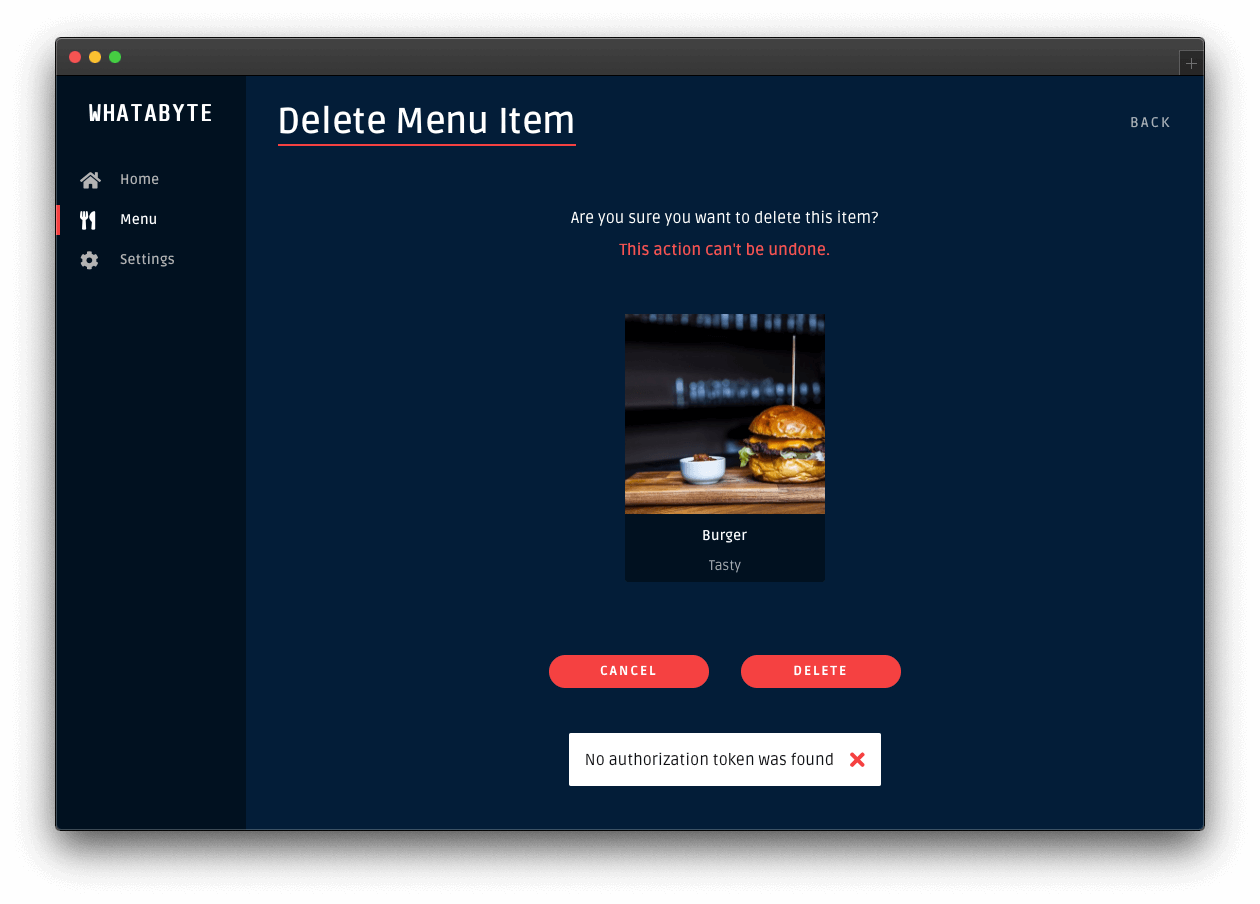
To continue with the rest of this tutorial, re-enable the demo client authentication features. Click on the Settings tab and click on the Modify button. The "Auth0 Demo Settings" page loads up. Enable the authentication features, fill out the necessary value, and click on the Save button.
"sample!"
Tweet This
“Combining Auth0’s developer-centric identity platform with the Okta Identity Cloud will drive tremendous value to both current and future customers,” said Todd McKinnon, Chief Executive Officer, and co-founder, Okta. “In an increasingly digital world, identity is the unifying means by which we use technology — both at work and in our personal lives. With so much at stake for businesses today, it’s critical that we deliver trusted customer-facing identity solutions. Okta’s and Auth0’s shared vision for the identity market, rooted in customer success, will accelerate our innovation, opening up new ways for our customers to leverage identity to meet their business needs.”
“I started my career as a developer,” McKinnon added. “Over the years, I’ve seen developers become more important than ever. They are the ones building every experience on the internet. Auth0’s DNA is rooted in developers, and I’ve always admired their sharp focus and leadership in developer-led identity.”
With continued global market tailwinds of cloud and hybrid IT, digital transformation, and zero-trust security, an identity platform has become one of the most critical technology investments an organization will make. These trends have accelerated over the past year as companies of all sizes and across every industry had to pivot quickly to deliver engaging customer experiences online. Organizations everywhere are rapidly leveraging identity to streamline processes, reduce costs, maintain the highest levels of security, and improve customer experiences to drive business growth. Okta and Auth0 are both committed to delivering innovation and value to organizations navigating those transformations.
“Okta and Auth0 have an incredible opportunity to build the identity platform of the future,” said Eugenio Pace, Chief Executive Officer, and co-founder, Auth0. “We founded Auth0 to enable product builders to innovate with a secure, easy-to-use, and extensible customer identity platform. Together, we can offer our customers workforce and customer identity solutions with exceptional speed, simplicity, security, reliability, and scalability. By joining forces, we will accelerate our customers’ innovation and ability to meet the needs and demands of consumers, businesses, and employees everywhere.”
Learn more about this announcement: https://www.okta.com/blog/2021/03/okta-auth0-powering-identity-for-the-internet/






